Category: Beginners’ Guide
-

Defender and attacker models in crypto security: key concepts explained
Why defender and attacker models matter in crypto security In crypto, security isn’t just about “strong encryption” anymore. The real question is: who exactly are you defending against, and what powers do they have? That’s where defender and attacker models come in. A defender model описывает, какие ресурсы, процессы и инструменты есть у команды защиты,…
-

How to identify legitimate crypto airdrops and partnerships safely
Why you should treat every airdrop as guilty until proven innocent Пока рынок гоняется за легкой халявой, злоумышленники тоже не спят: под видом щедрых раздач вытягивают seed-фразы, приватные ключи и доступ к кошельку. Поэтому любые legit crypto airdrops 2025 стоит воспринимать не как подарок вселенной, а как потенциальный риск, который нужно проверять по нескольким уровням….
-
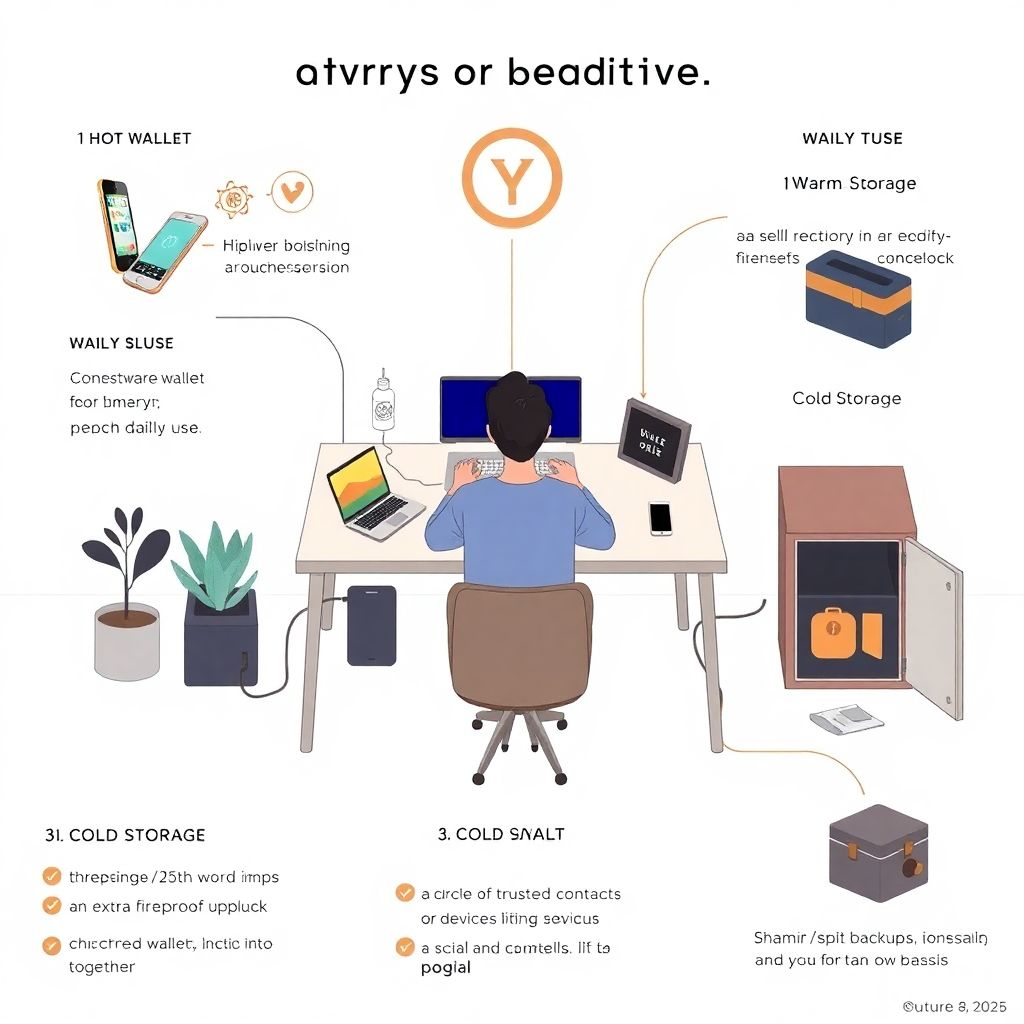
Crypto security basics: secure backups and device hygiene for your assets
Why crypto security feels so weird (and why you should care) If you lose your bank password, you click “reset” and yell at support if something goes wrong. If you lose your seed phrase, there is no support line, no chargeback, no legal department to lean on. That’s why crypto security feels more like running…
-

Compare staking yields across platforms to find the best crypto earning opportunities
Historical Context Staking has evolved alongside the growth of proof-of-stake (PoS) blockchains, which emerged as energy-efficient alternatives to proof-of-work systems. Initially introduced with projects like Peercoin and later popularized by Ethereum 2.0, staking enables token holders to participate in network security and consensus while earning passive income. As decentralized finance (DeFi) matured, numerous platforms began…
-
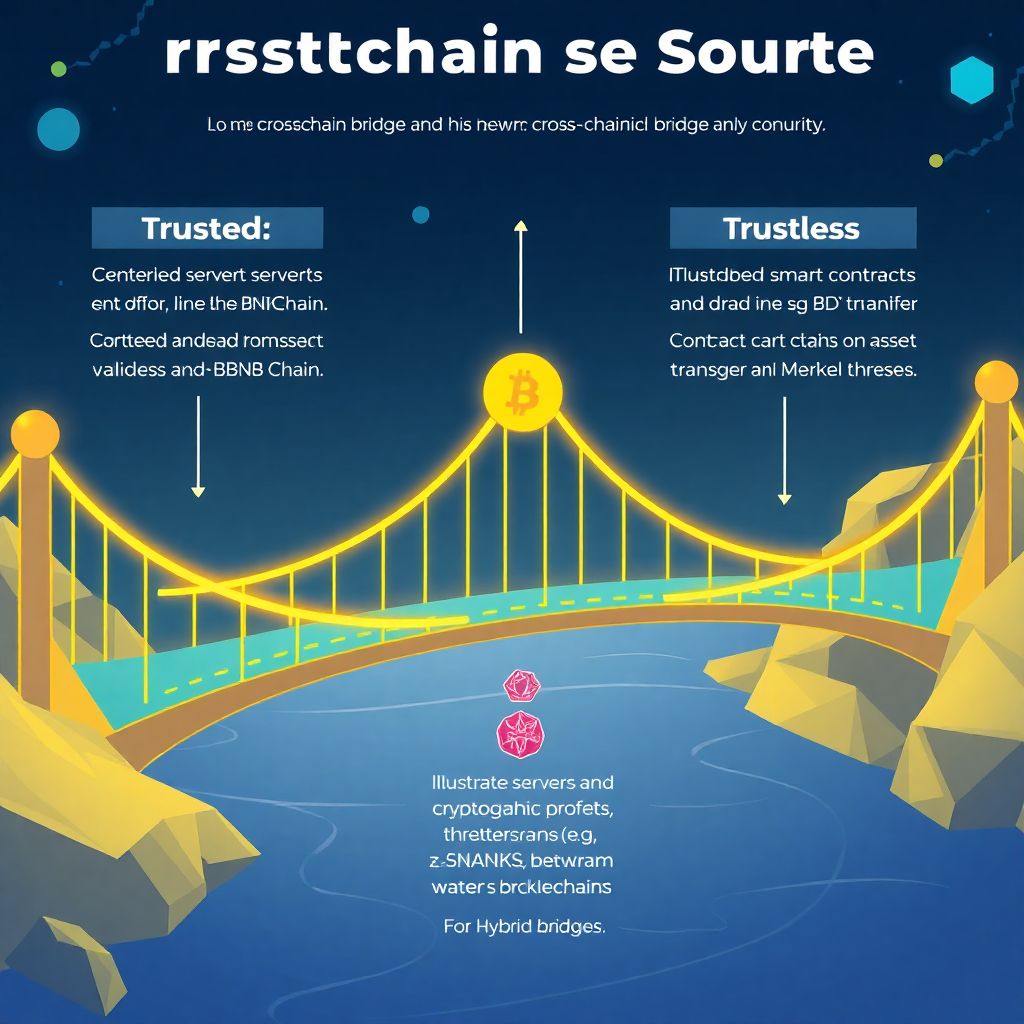
Cross-chain bridges security guide for beginners: how to understand and stay protected
Introduction to Cross-Chain Bridges Security Cross-chain bridges serve as critical infrastructure in the decentralized ecosystem, enabling interoperability between distinct blockchain networks. These protocols allow assets and data to move seamlessly across chains such as Ethereum, BNB Chain, Solana, and others. However, due to their complex architecture and reliance on external validators or smart contracts, bridges…
-
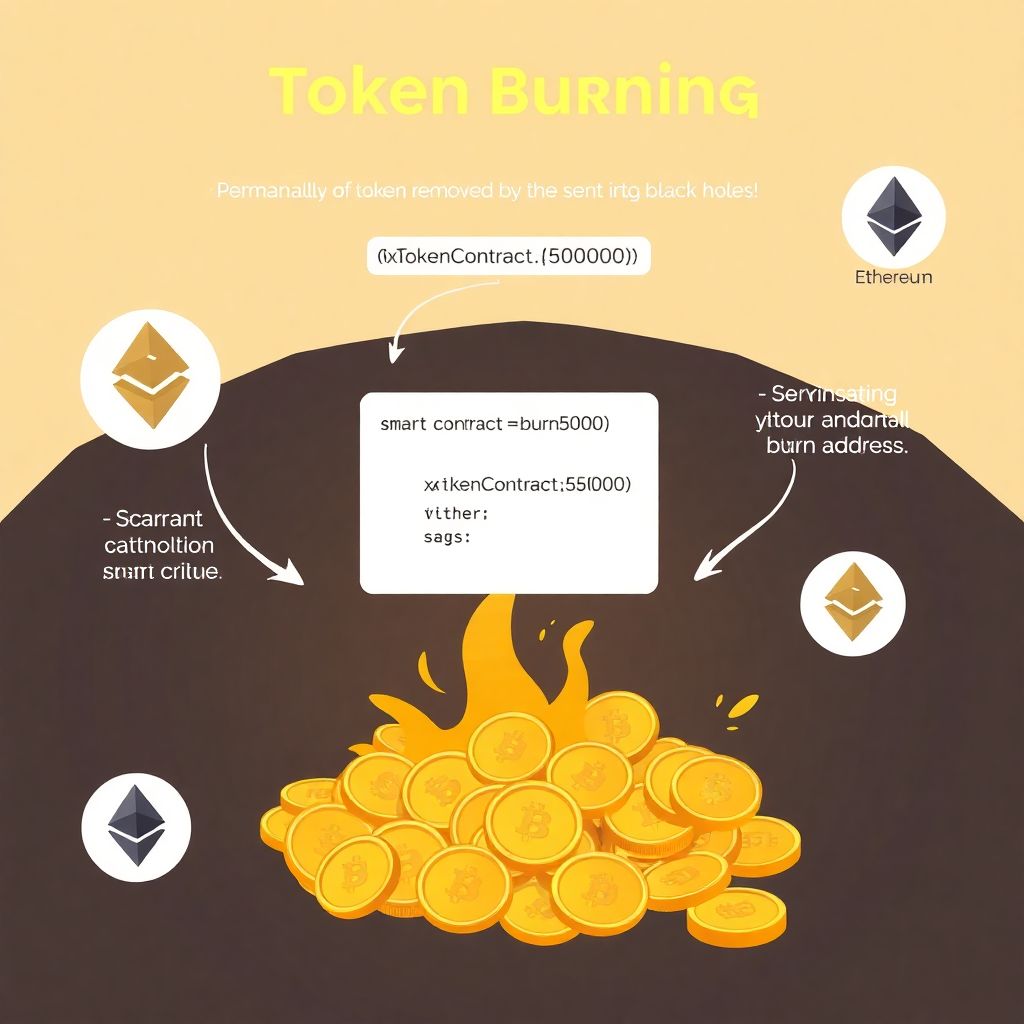
Token burn mechanics and economics explained in a beginner-friendly guide
What Is Token Burning? A Simple Yet Powerful Concept Token burning might sound like something destructive, but in the world of blockchain, it’s a strategic and often beneficial economic move. At its core, token burning refers to the process of permanently removing a certain number of tokens from circulation. These tokens are sent to a…
-

How to defend against social engineering attacks in crypto and protect your assets
Understanding Social Engineering in the Crypto Ecosystem In 2025, as cryptocurrencies continue to solidify their role in global finance, social engineering attacks have become increasingly sophisticated. Unlike traditional hacking, social engineering exploits human psychology rather than software vulnerabilities. In the crypto space, where transactions are irreversible and anonymity is common, such attacks can be especially…
-
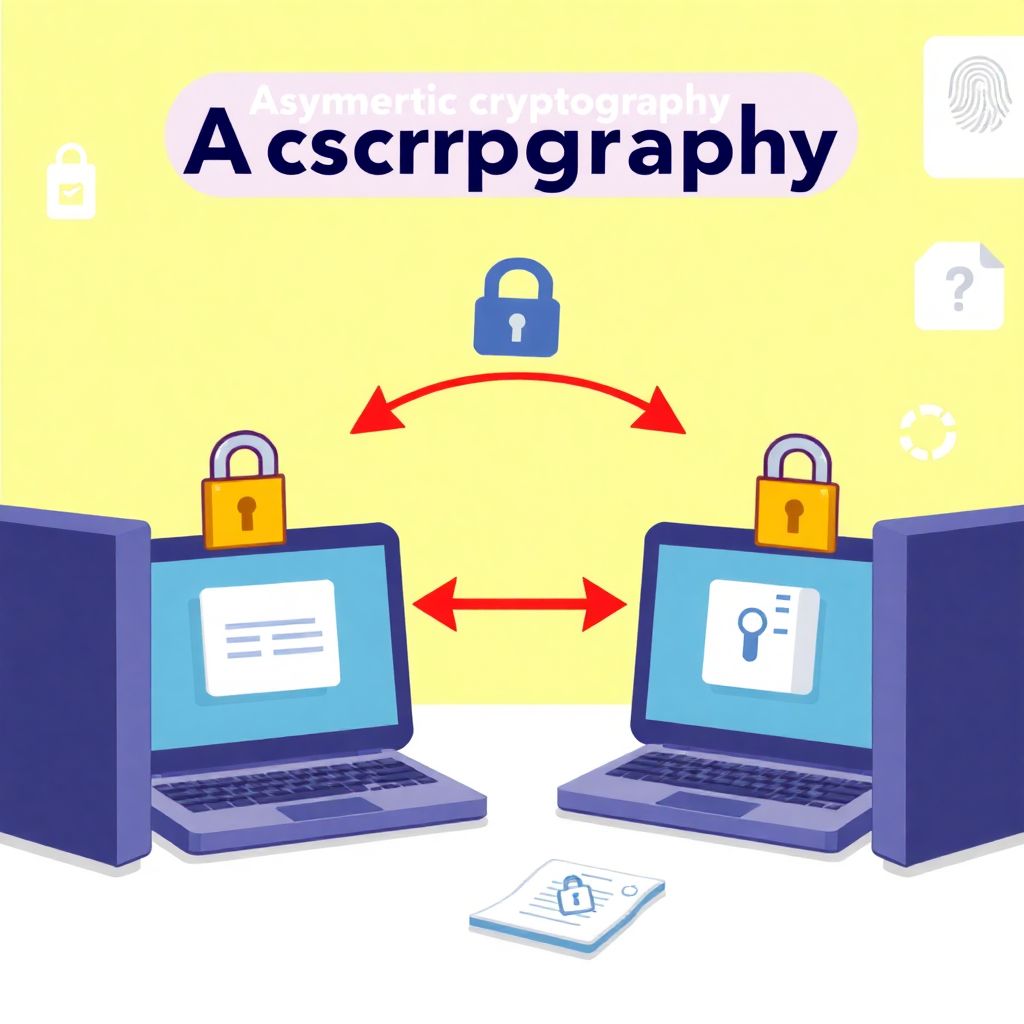
Asymmetric cryptography and digital signatures for beginners: a simple guide to get started
Understanding Asymmetric Cryptography Asymmetric cryptography, also known as public-key cryptography, is a foundational technology in modern digital security. Unlike symmetric cryptography, which uses one shared secret key, asymmetric cryptography relies on a pair of keys: a public key and a private key. The public key is used to encrypt data, while the private key is…
-

Crypto research for beginners: effective methods and trusted sources explained
Why Crypto Research Matters for Beginners Entering the world of cryptocurrency without proper research is like sailing in stormy waters without a compass. With over 25,000 cryptocurrencies listed on CoinMarketCap as of early 2024, it’s easy to fall victim to hype or misinformation. Many new investors rely on social media influencers or random tips, which…
-
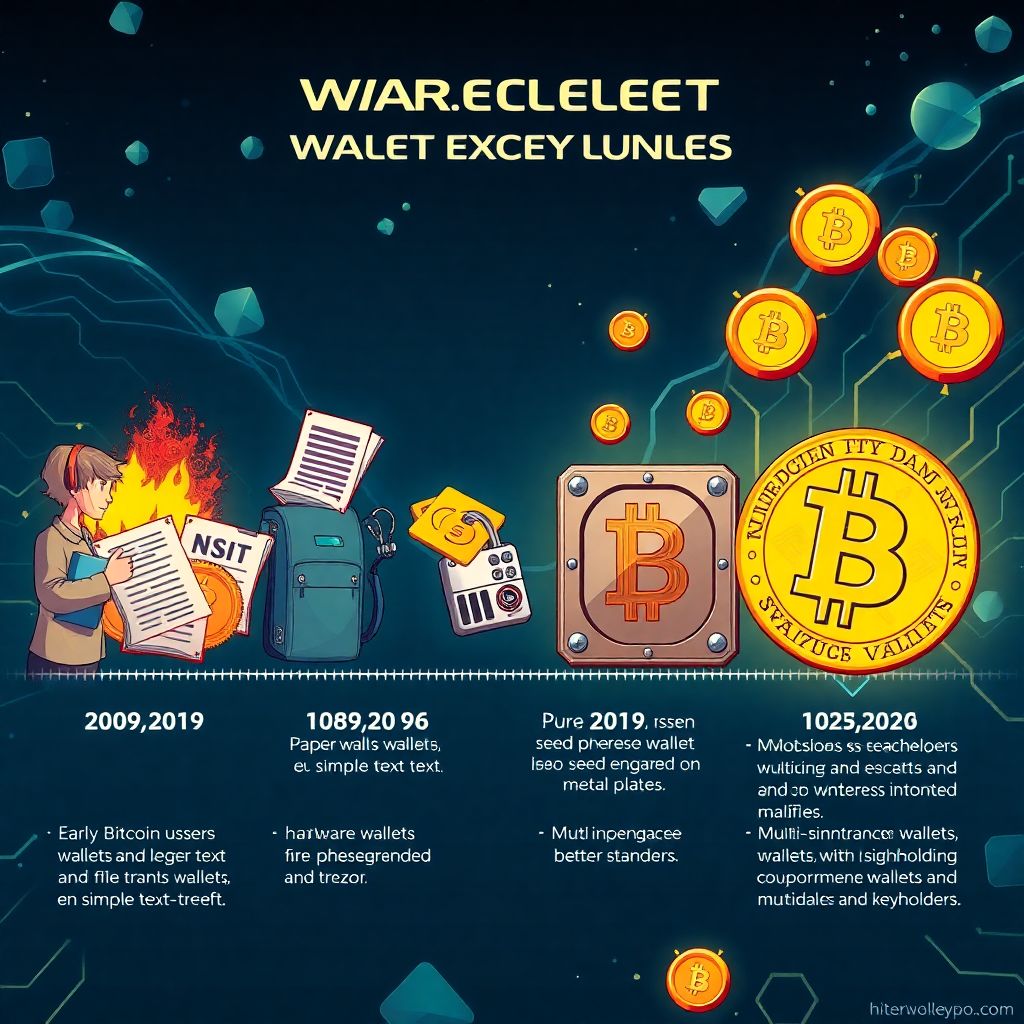
Secure crypto wallet backups: how to implement reliable protection for your assets
Historical Context and the Evolution of Crypto Wallet Backup Strategies Since the inception of Bitcoin in 2009, the challenges of secure cryptocurrency storage methods have evolved alongside the technology itself. Initially, users relied on simple text files or paper wallets to store their private keys—methods that were highly vulnerable to physical damage, theft, or loss….
