Why cryptographic signatures suddenly matter to everyone (including you)
In 2025, cryptographic signatures quietly sit behind almost everything you trust online: your banking app, software updates, messaging apps, even your car’s firmware. You don’t see them, but every time your device checks, “Is this really from who it claims to be, and was it changed on the way?” — that’s a cryptographic signature doing its job.
Think of a cryptographic signature as the digital version of a handwritten signature and a tamper-evident seal combined, but far more reliable and verifiable by machines at scale. Once you grasp how signatures and verification work, a lot of “security magic” stops looking mystical and starts looking like engineering you can understand, use, and even build on.
And that’s the goal of this guide: to give you a practical, intuitive understanding — without drowning you in math — and to show where this field is heading next.
—
The core idea: signing data so others can verify it
At its heart, a cryptographic signature answers three questions:
1. Who created this data?
2. Was it altered after signing?
3. Can I prove that in a way others will accept?
To do this, we use a key pair:
– A private key: secret, held by the signer.
– A public key: shared with the world so anyone can verify.
The signer runs data through a hash function (producing a short, unique fingerprint) and then uses their private key to sign that hash. The verifier uses the public key and the data to check that the signature is valid. If even a comma in the data changes, the verification fails.
That’s it. Everything else — from secure emails to blockchain transactions — is basically a sophisticated orchestration of this pattern at scale.
—
Inspiring real-world examples that don’t sound like textbook exercises
1. Software updates that can’t be silently hijacked
When your operating system or browser updates itself, you probably just click “Install” and move on. Behind the scenes, digital signature software verifies that the update actually came from the vendor and wasn’t replaced by malware during download.
This is exactly how the industry responded after high-profile supply chain attacks: vendors began requiring that *every* package, container image, and binary be signed and verified automatically in CI/CD pipelines. Teams discovered that signatures weren’t just a compliance checkbox — they were the single most reliable way to detect tampering before anything hit production.
2. Open-source communities protecting their reputations
Big open-source projects like Linux distributions, Kubernetes tools, and package managers now sign releases by default. Maintainers use signing keys; users verify them. When a popular library is compromised, a signed release history often becomes the forensic backbone: it tells you which versions you can still safely trust.
For many communities, adopting signatures was a turning point: contributors suddenly realized, “We’re not just writing code; we’re operating an infrastructure of trust.” That mental shift is powerful.
—
How signatures plug into the bigger security ecosystem
You rarely use signatures in isolation. They sit inside larger systems that help you answer a sneaky question: *“I see a public key… but who says it belongs to Alice and not to an attacker?”*
That’s where public key infrastructure solutions (PKI) come in. PKI ties public keys to real-world identities (people, domains, organizations) using certificates issued by trusted authorities. When your browser shows a padlock and connects over HTTPS, it’s validating a certificate and the server’s cryptographic proof that it holds the right private key.
Modern ssl certificate providers don’t just issue certificates for websites; they issue certificates for signing code, documents, containers, and even internal microservices. This is why cryptographic signatures feel “plugged into” browsing, email, VPNs, and beyond — the same trust backbone underpins all of it.
—
A practical mental model (without heavy math)
Here’s a simple way to think about cryptographic signatures and verification:
1. Hashing:
You compress the data into a fixed-length fingerprint. Any change in data → different fingerprint.
2. Signing:
You run that fingerprint through an algorithm using your private key. The result is the signature.
3. Verification:
Someone else recomputes the fingerprint and checks, with your public key, that:
– The signature matches the fingerprint.
– The public key really belongs to you (via PKI, Web of Trust, or explicit key exchange).
If both checks pass, the verifier knows:
– The data wasn’t altered (integrity).
– It came from whoever controls the private key (authenticity).
– The signer can’t later deny having signed it (non-repudiation), at least in a well-run system.
That’s the practical essence — every real-world system is just adding layers of distribution, governance, automation, and usability on top.
—
Where cryptographic signatures are quietly winning
Case 1: Secure software supply chains
A wave of incidents from 2020–2023 (SolarWinds, dependency hijacking, malicious NPM packages) finally pushed enterprises to treat software supply chains as critical infrastructure.
Many modern enterprise cryptography services now bundle:
– Automatic signing of artifacts in CI/CD.
– Policy engines that refuse to run unsigned or untrusted artifacts.
– Central dashboards showing “who signed what, when, with which key”.
Organizations that embraced this had a huge advantage: when a new vulnerability was announced, they could rapidly answer: *“Exactly where are we using this component, and which builds are cryptographically traceable?”* That level of visibility and assurance used to be science fiction.
Case 2: Code signing certificates as a business decision
For software vendors, code signing certificate purchase used to be a painful formality. Now it’s seen as a sales enabler and a trust anchor.
– Users get fewer scary warnings when installing software.
– OS vendors and app stores increasingly mandate signed binaries.
– Support teams spend less time convincing customers “Yes, this installer is really from us.”
Some smaller vendors discovered that simply adding robust code signing and clear documentation about their security practices increased conversion rates and reduced churn. Security turned into a visible product quality, not just a backend cost.
Case 3: Regulated industries and digital documents
Banks, legal firms, and healthcare providers are shifting away from paper and simple PDF signatures to fully verifiable cryptographic signatures, often integrated with identity providers and PKI.
This allows:
– Legally binding, cryptographically signed agreements.
– Audit trails where every edit and approval is traceable.
– Cross-border workflows where trust is rooted in standards, not just contracts.
You can think of it as “DocuSign with math you can verify,” instead of just trusting screenshots and logs.
—
How to actually start learning (without getting lost)

Let’s be very practical. If you want to *understand* and *use* cryptographic signatures — not necessarily design new algorithms — here’s a realistic path.
1. Build intuition with small, hands-on experiments
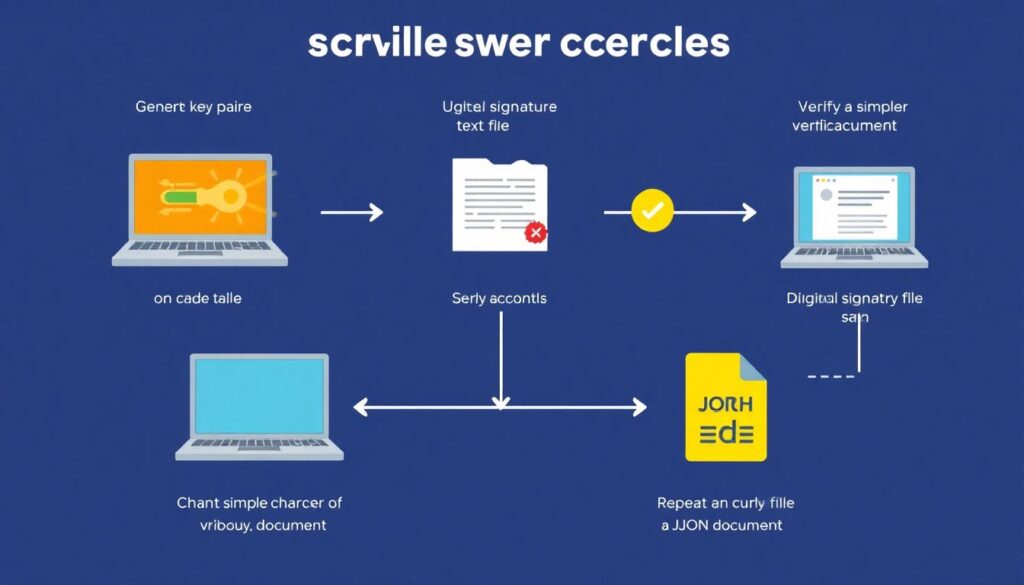
1. Generate a key pair on your machine (e.g., with `ssh-keygen`, `gpg`, or `openssl`).
2. Sign a simple text file.
3. Verify the signature on another machine or account.
4. Change a single character in the file, try verifying again, and observe the failure.
5. Now repeat this with a JSON document or a config file you actually care about.
This tiny loop already gives you more understanding than reading ten theoretical blog posts.
2. Read specs selectively, not religiously
Instead of reading standards end-to-end, focus on:
– What problem a given standard solves (e.g., JSON Web Signatures for APIs).
– Where the keys come from.
– How verification is supposed to be done *in your stack* (language, framework, cloud).
An analytical mindset helps: your main questions should be *“What’s the trust model here?”* and *“What assumptions are hidden?”* — not “What is the perfect algorithm?”
3. Use trusted libraries and opinionated tools
Avoid implementing crypto yourself. Modern digital signature software and libraries (in Go, Rust, Java, Python, etc.) usually offer high-level primitives:
– `sign(data, private_key)`
– `verify(data, signature, public_key)`
Your main job is to:
– Manage keys and certificates securely.
– Store metadata about what was signed and when.
– Automate verification in your pipelines and applications.
—
Recommendations for developing real expertise
If you’re serious about going deeper, approach this as a long-term skill-building process, not a weekend hack. Here’s a structured route:
1. Master the basics of asymmetric crypto & hashing
Understand why we use asymmetric keys for signatures, and why hash functions like SHA-256 are central.
2. Learn one practical PKI stack thoroughly
For example, a cloud provider’s certificate management + ACME + internal CA. Get comfortable issuing, rotating, and revoking certs.
3. Integrate signatures into one real project
Add artifact signing to a CI pipeline, or sign JSON web tokens with your own keys rather than a third-party service.
4. Study at least one failure story in depth
Read incident reports where signatures *were* or *weren’t* used. Ask: What went wrong in key management, governance, or verification?
5. Keep an eye on post-quantum developments
Even if you don’t implement them yet, track NIST’s post-quantum cryptography projects and how they influence signature schemes.
By following these steps, you’ll move from “I can copy-paste from Stack Overflow” to “I understand the trust boundaries of my system and can reason about them.”
—
Resources for learning (2025-friendly)
In 2025, the biggest challenge is not scarcity of information, but signal-to-noise. Here’s where the quality tends to be high:
– Books (conceptual + practical)
Look for titles that combine protocol explanations with real-world case studies, not just math-heavy treatments.
– Vendor and cloud provider documentation
Docs for AWS KMS, Azure Key Vault, GCP Cloud KMS, and major certificate authorities are full of real architectures, not just theory.
– Open-source projects and their security docs
Study how Kubernetes, Linux distributions, or popular package managers describe their signing and verification flows.
– Security-focused blogs and incident write-ups
Postmortems on supply chain attacks, CA incidents, or signing key leaks teach you what *actually breaks* in practice.
– Online courses and labs
Choose ones that include hands-on labs: generating keys, signing artifacts, and integrating with CI/CD or container registries.
Use these resources analytically: every time you learn a new mechanism, ask yourself, *“What threat does this reduce, and what assumptions does it rely on?”*
—
Forecast: where cryptographic signatures are heading by 2030
The next 5 years will be less about inventing entirely new ideas and more about scaling and simplifying what we already know works.
1. Ubiquitous, invisible signatures everywhere
You’ll increasingly see signatures attached to:
– Every container image and package by default.
– Every document in regulated workflows.
– Every internal microservice communication in serious enterprises.
Most end-users won’t know any of this exists; they’ll just experience fewer compromises and more reliable audit trails.
2. Post-quantum transition (quiet but massive)
The rise of quantum computing is pushing organizations to plan for post-quantum signature schemes. By 2030:
– Many critical infrastructures will run hybrid modes: both classical and post-quantum signatures.
– Major public key infrastructure solutions will support issuing and managing post-quantum certificates alongside traditional ones.
– Developers will use new algorithms via familiar APIs, but system architects will spend years managing the migration risk.
You don’t need to be a cryptographer, but you *do* need to understand that algorithms will change while the fundamental signing–verification model stays.
3. More regulation, more automation, less “optional” security
Expect regulations to require stronger attestation of software origin and data integrity, especially in finance, healthcare, and critical infrastructure. That means:
– Mandatory signing of critical software components.
– Automated verification pipelines enforced by policy, not by goodwill.
– Growing ecosystems of managed key, certificate, and signing services.
This will further expand the role of enterprise cryptography services that bundle key management, signing APIs, policy engines, and auditing under one roof.
4. “Trust transparency” as a competitive edge
Companies that can clearly show:
– What they sign.
– How they manage keys.
– How they verify third-party components.
…will stand out in a market weary of data breaches and supply chain attacks. Cryptographic signatures will become part of marketing narratives: *“Here’s how we can prove our software and data are authentic.”*
—
Bringing it all together
Understanding cryptographic signatures and verification in 2025 is less about learning obscure math and more about thinking clearly about trust:
– Who do you trust to hold keys?
– How are keys generated, rotated, and revoked?
– Where in your systems do you require proof that something is authentic and unaltered?
Once you see signatures as a practical tool for encoding these trust decisions, everything clicks. They stop being “security black magic” and become just another engineering primitive — like databases or message queues — except they manage trust instead of data or messages.
If you start now with a few small experiments, leverage modern tools, and stay curious about how real incidents unfold, you’ll be well-positioned for the coming decade of secure-by-default infrastructure. Cryptographic signatures will be everywhere; the real opportunity is for you to be one of the people who actually understands how and why they work.

