Understanding Cross-Chain Interoperability: A Practical Risk Guide
Interoperability between blockchains is a cornerstone for the future of decentralized finance and multi-chain ecosystems. However, the process of enabling communication between different blockchain networks is riddled with complexities and vulnerabilities. This guide focuses on identifying key risks, comparing existing approaches, and providing actionable advice for navigating the cross-chain landscape.
Common Approaches to Cross-Chain Interoperability
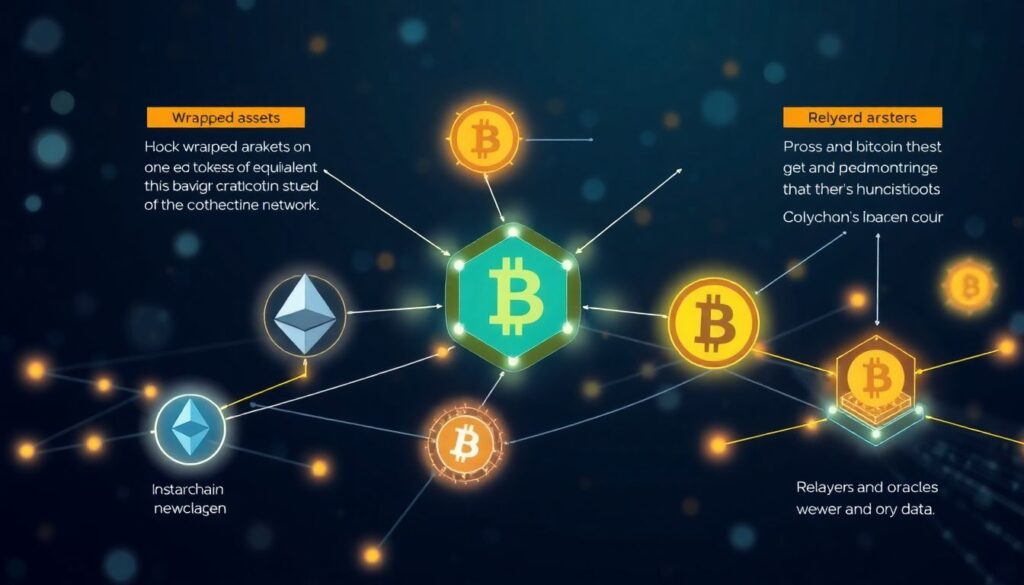
Several technical frameworks have emerged to facilitate communication across chains. The most prominent include:
– Wrapped Assets: These involve locking assets on one chain and issuing equivalent tokens on another (e.g., wrapped BTC on Ethereum).
– Relayers and Oracles: These off-chain services monitor events on one chain and report them to another, often used in cross-chain bridges.
– Light Clients and Zero-Knowledge Proofs: Advanced cryptographic methods that allow one chain to verify the state of another without trust in third parties.
Each method has its own trade-offs in terms of decentralization, scalability, and security. Wrapped assets are user-friendly but rely heavily on centralized custodians. Relayers offer flexibility but introduce new attack vectors. Light clients are secure but computationally expensive and complex to implement.
Frequent Mistakes by New Developers and Users

In the rush to build multi-chain applications or use cross-chain DeFi protocols, beginners often overlook several critical aspects:
– Underestimating Trust Assumptions: Many cross-chain bridges rely on validators or oracles that are not fully decentralized. Assuming all bridges are equally secure is a major pitfall.
– Poor Key and Asset Management: Users frequently lose funds by sending assets to incompatible addresses or by mismanaging wrapped tokens.
– Ignoring Latency and Finality Differences: Each blockchain has its own consensus and finality model. Failing to account for these differences can cause unexpected delays or transaction failures.
– Blind Trust in Audits: Just because a protocol was audited doesn’t mean it’s immune to exploits. Many high-profile bridge hacks occurred despite multiple audits.
Risks of Cross-Chain Bridges
Cross-chain bridges are particularly vulnerable, as they often become lucrative targets for attackers. The most common attack vectors include:
– Exploiting smart contract bugs in bridge contracts
– Compromising validator nodes or multisig wallets
– Using replay attacks across chains
Notable incidents like the Ronin Bridge and Wormhole hacks highlight the immense financial risk associated with insecure bridge infrastructure.
Pros and Cons of Leading Interoperability Technologies
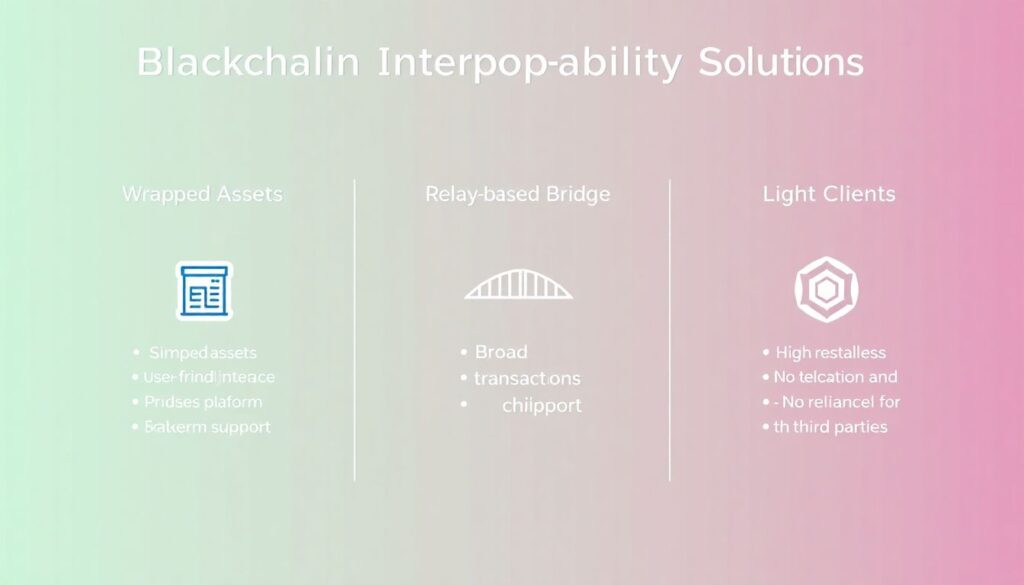
When evaluating interoperability solutions, it’s important to weigh their strengths and weaknesses:
Advantages:
– Wrapped Assets: Simple user experience, widely supported
– Relayer-based Bridges: Fast transaction confirmation, flexible architecture
– Light Clients: High trustlessness, no need for third-party validators
Disadvantages:
– Wrapped Assets: Centralized custody, risk of depegging
– Relayers: Vulnerable to manipulation, often semi-centralized
– Light Clients: High gas costs, complex to deploy and maintain
How to Choose the Right Interoperability Solution
Selecting the appropriate cross-chain strategy depends on your use case, risk tolerance, and technical resources. Consider the following:
– Security Over Speed: For high-value transfers, prioritize trust-minimized solutions like zero-knowledge bridges or light clients.
– Use Reputable Bridges: Always verify whether a bridge has been battle-tested and has transparent governance.
– Diversify Exposure: Avoid concentrating large amounts of value in a single cross-chain asset or bridge.
Key Recommendations
To mitigate cross-chain risks effectively:
– Use bridges with decentralized validator sets or cryptographic proofs
– Regularly monitor for protocol updates and disclosed vulnerabilities
– Keep up with community discussions and security bulletins
Cross-Chain Trends to Watch in 2025
The landscape of blockchain interoperability is rapidly evolving. In 2025, expect to see:
– Adoption of Modular Interoperability Protocols: Projects like Cosmos IBC and Polkadot XCM are pushing toward standardized, composable cross-chain communication.
– Increased Use of Zero-Knowledge Proofs: zk-based light clients are gaining traction for their security and privacy benefits.
– Bridge Aggregators: New platforms are emerging that route transactions through the most secure and cost-effective bridges automatically.
Additionally, interoperability will likely expand beyond token transfers to include smart contract calls and cross-chain DAO governance, further increasing complexity and potential risk.
Conclusion
Cross-chain interoperability holds immense promise, but it’s not without significant hazards. Developers and users must approach this space with a deep understanding of the underlying technologies, a critical eye for security, and a cautious strategy for managing risk. By avoiding common mistakes and staying informed about emerging trends, you can safely navigate the multi-chain future.