“`html
Why chain compatibility and bridge risk suddenly matter so much
“`
Back in 2017–2019 nobody really cared which chain your tokens lived on. You were either “on Ethereum” or you weren’t in the game. Fast‑forward to 2025 and you have dozens of serious L1s and L2s, rollups everywhere, app‑chains, modular stacks – and your assets are constantly moving between them.
That’s where bridges come in. And that’s also where beginners get hurt.
From 2020 to mid‑2024, on‑chain data (Chainalysis, DeFiLlama, L2Beat) shows over $3.5–4 billion lost in bridge and cross‑chain protocol exploits. In some years, bridges made up more than half of all DeFi hacks by value. So a crypto bridge risk assessment for beginners is no longer “nice to have” – it’s survival.
This guide is a practical, conversational walkthrough of how to evaluate blockchain bridge security, understand chain compatibility, and choose routes with the best cross chain bridges low risk available today.
—
“`html
Step 1: Get the big picture – what is a bridge, really?
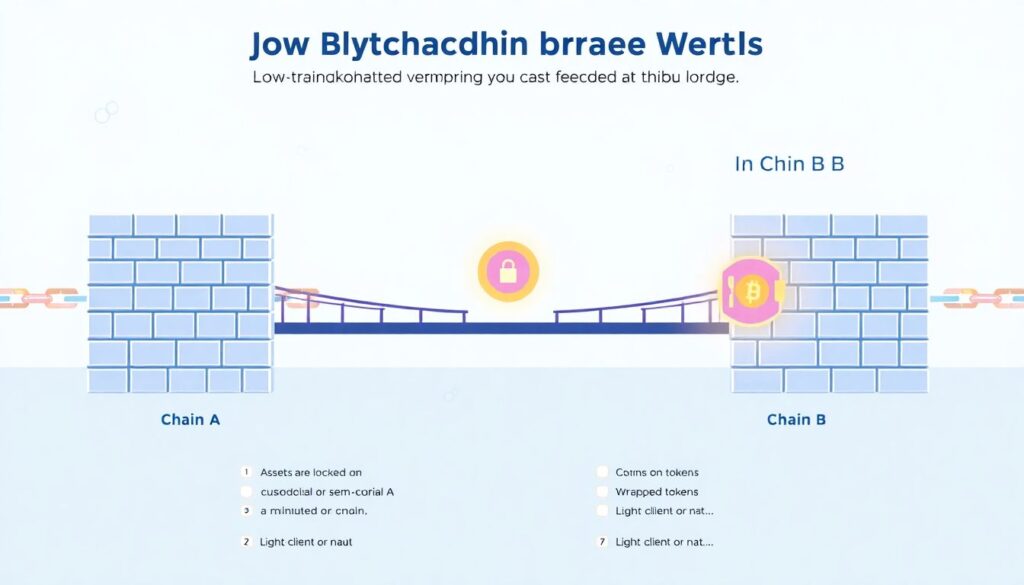
“`
In plain language:
A bridge lets you move value or information from one chain to another.
But under the hood, there are three very different philosophies:
– Lock‑and‑mint (custodial or semi‑custodial)
Assets are locked on chain A, and a wrapped version is minted on chain B.
– Light‑client or native verification
One chain verifies the state of the other directly on‑chain (no big trusted middleman).
– Liquidity networks / fast bridges
Liquidity providers front you tokens on the destination chain and settle later using various mechanisms.
Short version:
Bridges are either trust‑heavy but simple, or trust‑minimized but complex. Your risk lives in that trade‑off.
—
“`html
A quick historical detour: how we got to 2025
“`
To make sense of risk today, it helps to see the timeline:
– 2016–2019: Early experiments
Sidechains and federations (e.g., early Bitcoin sidechains, PoA bridges) were mostly centralized multisigs. Small TVL, little scrutiny.
– 2020–2021: DeFi boom & wrapped mania
Huge growth of wrapped BTC on Ethereum and simple token bridges to new L1s. TVL in bridges shot past $20B at the peak. Security practices lagged behind capital inflows.
– 2021–2023: The “bridge hack era”
Ronin, Wormhole, Nomad, Horizon, BSC Token Hub, and others — individual losses up to $600M+. Regulators and institutions started singling out bridges as systemic risk. Security budgets finally went up.
– 2023–2025: Toward modular and native solutions
Rollup ecosystems (OP Stack, zkSync, Arbitrum Orbit, Cosmos SDK app‑chains) start shipping more native bridges and IBC‑style protocols. Shared sequencing and interoperability layers reduce some classes of risk, but complexity explodes.
By 2025, we’re in a mixed world:
Some ecosystems rely on canonical bridges with strong guarantees; others are still dominated by 3rd‑party cross‑chain routers of varying quality.
—
“`html
Step 2: Understand chain compatibility before you even touch a bridge
“`
Most beginners jump straight to “Is this bridge safe?” That’s actually step two. First you should ask:
> “How compatible are these chains in the first place?”
Longer answer:
– Execution compatibility
Are both chains EVM‑based? Are they using similar virtual machines or completely different stacks (e.g., EVM vs. Move vs. CosmWasm vs. Solana runtime)? Closer execution models generally make safer, simpler bridges.
– Consensus and finality
– Does the source chain have probabilistic finality (like classic PoW or some PoS) or deterministic finality (like many BFT‑style chains)?
– How long before blocks are truly irreversible?
Slow, probabilistic finality can increase bridge complexity and attack windows.
– Data availability and rollback risk
If either chain can be rolled back or censored cheaply, bridged assets inherit that risk. That’s especially important with young L2s and app‑chains that may rely heavily on a small validator set or single sequencer.
– Native interoperability features
Ecosystems like Cosmos (IBC), Polkadot (XCM), and some rollup stacks have native cross‑chain messaging with stronger built‑in guarantees than many “bolt‑on” bridges between unrelated chains.
This is what people mean when they talk about blockchain chain compatibility and bridge comparison:
You’re not only comparing bridges; you’re comparing how well the underlying chains are designed to talk to each other at all.
—
“`html
Practical checklist: chain compatibility red flags
“`
Before you bridge, quickly look for:
– One chain is very new (launched in the last 6–12 months) with low validator diversity.
– The chain has had multiple halts or rollbacks in the last year.
– Finality is vague, undocumented, or depends on “social consensus” without clear parameters.
– The bridge docs don’t explain how they handle reorgs / rollbacks on the source chain.
If you see more than one of these, treat any bridging to that chain as high‑risk speculation, not routine fund management.
—
“`html
Step 3: A beginner‑friendly framework for bridge risk
“`
Instead of memorizing dozens of project names, learn a mental model. Here’s a guide to choosing safe cross chain bridges based on five questions.
“`html
1. Who or what decides that a message is valid?
“`
This is the heart of how to evaluate blockchain bridge security.
In practice, you’ll encounter:
– Multisig / validator committee bridges
A fixed group (say 5–30 entities) signs off that assets are locked and messages are valid.
– Pros: Simple, usually fast.
– Cons: Single governance layer to compromise. If enough keys are hacked or collude, your funds vanish.
– Light‑client / on‑chain verification bridges
The destination chain verifies source‑chain headers and proofs directly.
– Pros: Trust‑minimized; very hard to fake without breaking the source chain itself.
– Cons: More complex, sometimes more expensive in gas, and not always available.
– Liquidity / message networks with their own consensus
Think of them as separate coordination layers that route value.
– Pros: Very fast and flexible.
– Cons: You must trust their security model and token economics as much as — sometimes more than — the chains you use.
As a beginner, favor architectures that verify chain state directly on‑chain rather than “just trust our validators.”
—
“`html
2. How concentrated is control?
“`
Bridges with:
– 2–5 signers, many of them closely linked,
– Upgrade keys held by a single team wallet, or
– A single operator/sequencer with broad powers
…are inherently fragile. In 2021–2023, several of the biggest hacks came from private key compromise of a small set of signers.
Look for:
– Public docs on the number of signers / validators.
– Clear explanation of upgrade mechanisms and time‑locks.
– Evidence of external, independent participants (not just team‑controlled entities).
—
“`html
3. Is the code battle‑tested and transparent?

“`
When you evaluate bridges:
– Prefer open‑source implementations with active repos.
– Check if contracts are verified on explorers.
– Look for multiple reputable audits (and read the audit dates, not just the logos).
– See whether high‑value ecosystems (Ethereum, major rollups, big L1s) officially support or endorse that bridge.
By 2025, the pattern is clear: the largest, most enduring bridges are typically the ones used as canonical by big ecosystems. That doesn’t make them risk‑free, but it’s a useful signal.
—
“`html
4. What’s the economic incentive and the worst‑case payoff?
“`
Think like an attacker:
– How much TVL is locked in the bridge today?
– How much liquidity sits on destination chains?
– Are there any caps or circuit breakers limiting outflows?
A bridge holding $1B+ with no withdrawal caps, minimal monitoring, and centralized control is a massive honeypot. Attackers only need to succeed once.
Healthy signs in 2025:
– Withdrawal rate limits, especially for new chains.
– Insurance or backstop funds with clear policies.
– Real‑time monitoring and alerting around large or unusual transfers.
—
“`html
5. Social and regulatory layer: who takes responsibility?
“`
Economic aspects matter beyond code:
– Is there a legal entity or consortium behind the bridge that can be held accountable?
– Are there terms of use, clarity on jurisdiction, and any commitment to compensation if something goes wrong?
– Have large institutions integrated the bridge, or is it mostly used by degen yield farmers?
You’re not guaranteed a bailout — far from it — but the presence of real‑world accountability slightly reduces tail risks and speeds up recovery in some failure scenarios.
—
“`html
Concrete steps: doing a crypto bridge risk assessment for beginners
“`
Here’s a minimal, repeatable process you can apply any time you’re about to bridge:
“`html
Before you click “Bridge”
“`
– Google the bridge + “exploit / hack / incident”
If you see big red flags from the last 6–12 months, stop and reassess.
– Check TVL and chain support on DeFi analytics sites
If TVL is tiny and there’s no meaningful user base, assume higher experimental risk.
– Find documentation and audits
– No docs? Red flag.
– One audit from 2021 for a heavily upgraded system? Also a red flag.
“`html
During the first use
“`
– Start with small test amounts.
– Double‑check destination addresses and chain IDs in wallet pop‑ups.
– Confirm official URLs via multiple sources (official X / website / reputable dashboards). Phishing is rampant.
“`html
As you become a regular user
“`
– Diversify: don’t park all your net worth on a single bridge or on one destination chain.
– Periodically move idle funds back to better‑secured base layers (e.g., Ethereum mainnet, the canonical chain for your assets).
– Stay joined to official bridge and chain channels to hear about halts, upgrades, and incident reports quickly.
—
“`html
Economic and industry‑wide implications of bridge risk
“`
Bridge design isn’t just a technical curiosity; it shapes capital flows across the entire crypto economy.
Capital efficiency vs. safety
– Capital efficiency:
– Fast, flexible bridges let liquidity chase yields across chains, equalizing interest rates and DeFi returns.
– Market makers can exploit arbitrage quickly, tightening spreads and improving pricing for regular users.
– Safety:
– Every additional bridge and chain introduces another surface for catastrophic loss.
– After big hacks, we often see sharp TVL outflows and long‑term stunting of the affected ecosystems.
This tension drives innovation:
Protocols in 2024–2025 increasingly seek native, low‑trust mechanisms that maintain efficiency without recreating the same custodial honeypots.
Institutional adoption and regulation
Institutions and regulated entities that entered crypto around 2021–2024 are far more bridge‑averse than retail. In 2025:
– Many institutions forbid non‑canonical bridges by policy.
– Risk teams maintain internal whitelists based on their own bridge risk frameworks.
– Regulators in multiple regions now explicitly call out cross‑chain movement as a higher‑risk activity in AML and consumer‑protection guidance.
The net effect:
Bridges that don’t invest heavily in security, transparency, and governance find themselves cut off from the “serious money” over time.
—
“`html
Forecasts for 2025–2030: where bridges and compatibility are headed
“`
Looking ahead from 2025, several trends seem likely:
1. Fewer, more dominant core bridges; more local, niche ones
– Expect a small set of systemically important bridges between major hubs (Ethereum mainnet, major rollups, a few strong L1s).
– Around them, many lighter‑weight, domain‑specific bridges for gaming, app‑chains, or enterprise networks.
2. Rise of native interoperability and shared security
– Cosmos‑style IBC, Polkadot’s XCM, and rollup‑native bridging will continue to grow.
– Bridges that piggyback on shared security from battle‑tested chains should gradually capture more TVL.
3. More formal standards for security and disclosures
– Think of “bridge security ratings” and standardized disclosures (validator set, upgrade keys, caps) similar to bond ratings or app‑store permissions.
– Analytics sites will likely offer structured bridge comparisons by 2026–2027.
4. Stronger economic backstops
– Protocols will increasingly build insurance funds, slashing mechanisms, and proof‑of‑reserve style attestation.
– Bridges without robust economic defenses will be viewed as incomplete.
5. User experience: bridges fade into the background
– Wallets and aggregators will route across multiple bridges automatically, surfacing only effective risk level and cost to users.
– Under the hood, these systems will rely on sophisticated blockchain chain compatibility and bridge comparison logic you never see.
If this plays out, you’ll spend less time choosing individual bridges and more time choosing trust profiles (e.g., “fast & cheap but higher risk” vs. “slow & ultra‑safe”), much like you choose shipping options online today.
—
“`html
Putting it all together: a simple mental model for beginners
“`
To keep it practical, here’s a compact way to think about everything above.
When evaluating cross‑chain options:
– Treat chains like jurisdictions and bridges like border checkpoints. Some borders are militarized and strictly controlled; others are a couple of cones and a guard with a flashlight.
– For your core holdings, prefer:
– High‑maturity chains.
– Canonical or native bridges with on‑chain verification and strong governance.
– Clear documentation, audits, and some level of institutional usage.
– For experiments and yield chasing:
– Assume money can go to zero.
– Limit size, diversify across different bridges and chains.
– Track news closely and move quickly if risk profiles change.
In other words, the best cross chain bridges low risk are usually not the trendiest or the fastest — they’re the ones that are boring, transparent, and deeply integrated into their ecosystems.
By internalizing this framework, you’ll be able to navigate 2025’s multi‑chain world with far more confidence, ask better questions, and drastically reduce your odds of learning about bridge risk the hard way.

