Historical Context
The need for personal crypto security playbooks became apparent during the rapid expansion of the cryptocurrency market in the 2010s and early 2020s. Major breaches — from Mt. Gox in 2014 to the Ronin Bridge hack in 2022 — exposed the fragility of centralized platforms and the risks of poor user practices. As adoption grew, so did the sophistication of attacks, with phishing, SIM swapping, and seed phrase theft becoming common threats to individual investors. By 2025, the crypto ecosystem has matured, regulatory clarity has increased, but the responsibility for self-custody and security still largely rests on individual users.
Fundamental Principles
A robust crypto security playbook is built upon several foundational principles. First and foremost is the concept of self-custody — holding private keys securely and independently. This requires understanding hot vs. cold storage, using hardware wallets, and employing multisig solutions where applicable. Secondly, operational security (OpSec) is crucial: minimizing digital footprints, avoiding oversharing, and securing communication channels. Lastly, regular updates and reviews of one’s security setup are essential to adapt to evolving threats and vulnerabilities.
Implementation Examples
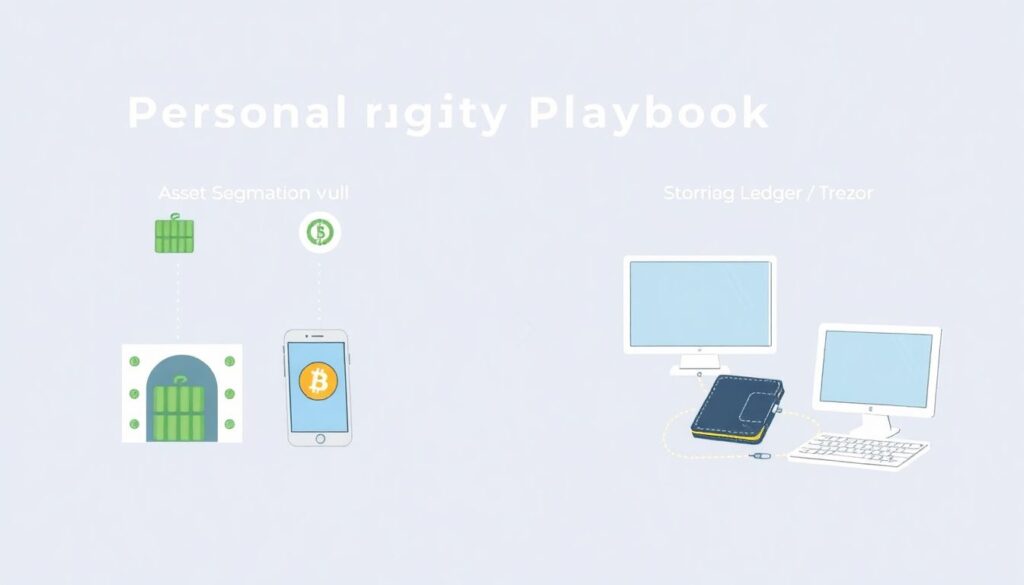
To build a personal crypto security playbook, follow a step-by-step approach tailored to your risk tolerance and asset value:
1. Segment your assets — Separate long-term holdings (cold storage) from active funds (hot wallets).
2. Use a hardware wallet — Devices like Ledger or Trezor provide secure offline key storage.
3. Secure backups — Store seed phrases in tamper-proof metal backups, in separate physical locations.
4. Enable 2FA and password managers — Use unique, complex passwords and hardware-based 2FA like YubiKeys.
5. Monitor activity — Utilize wallet tracking tools and set up alerts for unauthorized access.
6. Educate and simulate — Regularly train yourself on phishing detection and simulate recovery drills.
Each of these steps is an integral part of a living document — your playbook — which should evolve as your portfolio and the threat landscape change.
Common Misconceptions
Many users mistakenly believe that using a hardware wallet alone makes them invulnerable to attacks. In reality, social engineering, phishing, and poor recovery phrase handling remain huge risks. Another frequent error is storing seed phrases digitally — whether in cloud storage, note-taking apps, or screenshots — which exposes them to malware and hacks. Overconfidence in browser-based wallet extensions is also dangerous, as they are frequent targets of supply chain attacks. Lastly, assuming that regulatory protections in 2025 offer full recourse for lost or stolen crypto assets is misguided; decentralized finance remains largely self-sovereign and unforgiving.
Looking Ahead: Crypto Security in 2030

By 2030, personal crypto security will likely become as normalized as personal banking hygiene is today. Biometric authentication, decentralized identity (DID), and smart contract-based inheritance protocols are expected to become standard. AI-driven threat detection tools will proactively warn users of suspicious activity. However, as automation increases, so does the complexity of threats, with adversarial AI and quantum computing posing new challenges. The future demands that individuals not only follow best practices but also remain agile learners. Your crypto security playbook will no longer be a static guide — it will be a dynamic interface between technology, behavior, and continuous adaptation in a decentralized world.

