Why cross‑chain suddenly matters in 2025

If you joined crypto in the last year or two, you probably noticed something odd: everyone talks about “multichain,” but your coins still feel stuck on separate islands. You have ETH on Ethereum, cheap tokens on Base or Arbitrum, maybe some SOL on Solana, and a DeFi position on Polygon, yet moving value between them still feels like juggling hot potatoes. That gap between how marketing describes Web3 and how it actually works is exactly where cross‑chain interoperability comes in. In 2025, we are finally seeing the first real wave of production‑ready protocols that let blockchains talk to each other in a way that is not only fast, but also much safer than the wild‑west bridges of 2021–2022, when hacks regularly burned hundreds of millions of dollars in a single night.
Today, cross‑chain is not just about “moving tokens around.” It is turning into a full communication layer for smart contracts: apps on one chain can trigger logic on another, settle payments elsewhere, or borrow liquidity from networks you never directly touch. That is why people keep searching for cross chain interoperability explained in simple language. Users are tired of buzzwords and just want to understand: “How do I move my coins without getting wrecked, and what’s changing compared to a few years ago?” Let’s walk through that, step by step, with a focus on how things actually work in 2025, not just in whitepapers.
—
What “cross‑chain interoperability” really means (in plain English)
At a human level, interoperability is simple: you want your assets and apps to work no matter which blockchain they live on. Right now, every major chain is like a separate country with its own roads, banks, and rules. Ethereum has the deepest DeFi, Solana pushes high‑throughput trading, Bitcoin remains the value bunker, and rollups like Arbitrum, Optimism, Base, zkSync and Scroll offer cheaper execution attached to Ethereum. Cross‑chain interoperability is the set of roads, airports, customs officers, and communication cables that connect these “countries” without you having to sell and rebuy everything each time you cross the border.
When people say “cross‑chain,” they can mean three slightly different things. First, moving tokens (what most beginners care about). Second, messaging between smart contracts (for example, an app on Optimism that settles its accounting on Ethereum mainnet). Third, shared security, where multiple chains rely on the same validator or restaking set, like EigenLayer‑secured services or Cosmos chains renting security from a provider. In 2025, real innovation is happening mostly in the second and third categories, but user interfaces still hide that complexity behind simple “Bridge” or “Send” buttons, which is why getting cross chain interoperability explained clearly matters so much.
—
How bridges used to work — and why so many of them got hacked
The first big wave of bridges (think 2020–2022) worked like glorified custodians. You locked your tokens on Chain A, a set of off‑chain or semi‑trusted relayers confirmed this, and then the bridge minted “wrapped” versions of your tokens on Chain B. It was simple to use but introduced huge attack surfaces. If the validators, multisig, or smart contracts running that bridge broke, an attacker could mint infinite fake wrapped tokens or drain the locked assets. That is exactly what happened over and over: the Ronin bridge exploit (~$620M), Poly Network (~$610M), BSC Token Hub (~$570M), Wormhole (~$325M) and many smaller incidents. Across 2021–2023, cross‑chain hacks cost the ecosystem more than $2.5B according to multiple security reports.
The main problem was that each bridge was its own mini‑bank with its own security assumptions. Some relied on a 5‑of‑9 multisig; others used small validator sets; some had upgrade keys controlled by a single company. One bug or one compromised key, and everything collapsed. This is why, when you research best cross chain bridges for beginners in 2025, you will see a huge shift toward protocols that reuse the security of major chains (Ethereum, Cosmos Hub, Bitcoin) instead of inventing their own fragile trust models. The lesson from that era is blunt: if your bridge’s security guarantees are weaker than the chain you are bridging from, you are effectively downgrading your protection every time you move funds.
—
Modern cross‑chain architectures: from ad‑hoc bridges to shared security
Around 2023–2025, the industry slowly moved from “build a custom bridge for everything” to “build generic cross‑chain layers.” Instead of ten different bridges between Ethereum and Solana, the idea is to have standardized messaging layers that any app can plug into, with clear security assumptions and battle‑tested implementations. The Inter‑Blockchain Communication protocol (IBC) in Cosmos pioneered the concept of light‑client‑based communication, where each chain directly verifies the other’s consensus. Ethereum’s rollup ecosystem added another pattern: rollups regularly post their state roots to Ethereum, so Ethereum can act as a sort of security and data anchor.
In parallel, a new wave of protocols like LayerZero, Wormhole (v2+ with guardian set hardening), Hyperlane, Axelar, Chainlink CCIP and others positioned themselves as generic interoperability layers rather than just bridges. They focus on reliable cross‑chain messaging, with token transfers being just one application built on top. At the same time, restaking and shared security platforms emerged: EigenLayer on Ethereum lets cross‑chain services reuse staked ETH as economic backing, while Cosmos chains can rent security through solutions like Cosmos Hub’s replicated security or mesh security designs. All that means that a cross chain interoperability solutions comparison in 2025 is no longer just “Which bridge has the best APR?” but “Which system plugs into the deepest, most decentralized security and offers clear, verifiable guarantees?”
—
Technical details: three main models of cross‑chain security
Below is a compact breakdown of how modern cross‑chain systems usually secure messages and token transfers. This is the “under the hood” view that most interfaces hide, but understanding it helps you evaluate risk.
1. Light‑client based (on‑chain verification).
The receiving chain runs a light client of the sending chain, verifying headers and Merkle proofs directly in its own smart contracts. This is what IBC does in Cosmos and what some Ethereum rollup bridges are evolving toward. Security level: as strong as the underlying consensus, but potentially expensive in gas if not optimized, especially for complex chains like Ethereum.
2. External validator / oracle sets.
A separate network of validators (or oracles) observes multiple chains and signs messages when they are finalized. The receiving chain only needs to verify aggregated signatures from this set. Wormhole’s guardians, Chainlink’s oracle network and several CCIP‑style systems follow this model. Security depends on the size, decentralization and incentives of this external set, plus any restaking or slashing rules attached to it.
3. Multisig / permissioned operators.
A small group of known entities (for example, 4–15 signers) confirm cross‑chain events and authorize mints or unlocks on the destination chain. This is the simplest and cheapest setup technically but the weakest in terms of decentralization and censorship resistance. Many legacy bridges used this pattern, and a surprising number still do, often hidden behind pleasant UX.
In practice, some protocols combine these models: you might see a system where a validator set is economically secured through restaked ETH, plus optional light clients for the highest‑value routes, providing multiple layers of verification when large transfers are involved.
—
How to transfer crypto cross chain safely in 2025
From a user’s point of view, the process of how to transfer crypto cross chain has finally become less painful, but the decisions you make before clicking “Send” still matter. The first choice is where you start: many wallets (Rabby, MetaMask with Snaps, Phantom, OKX, OneKey, etc.) now integrate cross‑chain routing directly, so you might not even open a standalone bridge site. Instead, you choose “Send from Ethereum to Base,” pick a token, and the wallet negotiates the route, often spanning multiple protocols under the hood. This convenience is great, but you still need to understand who is actually securing that transfer.
A practical rule in 2025: for significant amounts, prefer routes that either use canonical rollup bridges (for L2↔Ethereum) or well‑audited, high‑liquidity interoperability layers that publish clear security docs and on‑chain metrics. For smaller amounts (under a few hundred dollars), time and gas fees may matter more than deep‑theory trust assumptions, and it is reasonable to choose faster or cheaper options. However, always double‑check URLs, especially if you get a link from social media or a random Discord. Phishing is still more common than protocol‑level hacks, and a fake bridge UI can drain your wallet in one transaction.
—
Step‑by‑step: a beginner‑friendly cross‑chain transfer
1. Choose your networks.
Decide where you are sending from and where you are going. For example, you might want to move USDC from Ethereum mainnet to Arbitrum to farm yield with lower gas fees, or from Solana to Base to use a specific on‑chain game.
2. Pick a wallet with good cross‑chain support.
Use a wallet that clearly shows networks and tokens and supports multiple chains. In 2025, many wallets automatically detect which bridge or router is most suitable, but they also typically offer an “advanced” view so you can see what protocol they are using in the background.
3. Check bridge reputation and audits.
Before approving anything, quickly look up the protocol name on reputable sources: docs, security audits, bug bounty programs, and if possible, historical uptime and incident reports. If you see zero public information or only marketing buzz, consider that a red flag.
4. Start with a small test transfer.
Send a tiny amount first: enough to cover fees and confirm the system works, but not enough to hurt if it gets stuck. This is your real‑world smoke test for that particular route.
5. Review fees and timing.
Check the estimated arrival time, minimum amount, and total cost, including gas at both ends and any protocol fee. Some routes may look cheap but require multiple on‑chain approvals, or they might use illiquid pools that introduce high slippage when they bundle swaps with bridging.
6. Confirm on both chains.
After the transfer is “completed” in the UI, verify your new balance directly in the wallet or block explorer of the destination chain. Do not assume success just because a progress bar hit 100%; explorers like Etherscan, Arbiscan, Solscan or their equivalents remain your best source of truth.
—
Technical details: where the money actually moves
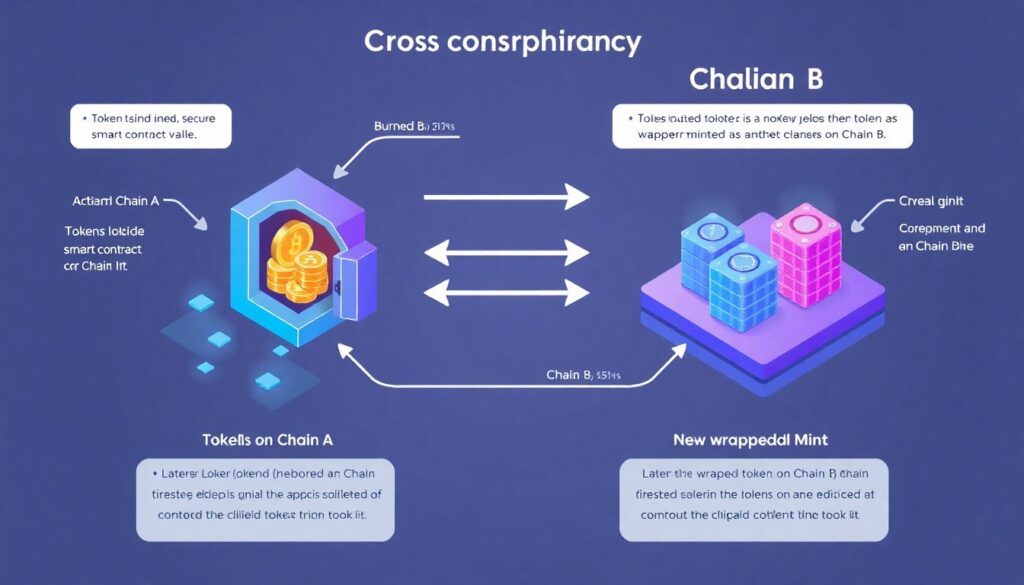
Under the hood, most cross‑chain transfers follow one of two patterns. The first is classic “lock and mint”: your tokens on Chain A are locked in a smart contract (or burned at the protocol level), and a representation is minted on Chain B. You can later burn those wrapped tokens on Chain B to unlock the original on Chain A. The risk here is concentrated in the contract that holds the locked funds and the mechanism that mints or burns the wrapped version.
The second pattern is “liquidity networks” or “liquidity routing.” Instead of shipping the same token instance between chains, routers rebalance pools. If someone wants to move USDC from Ethereum to Base, they effectively swap their USDC into a router pool on Ethereum, and someone else (or the router itself) pays out USDC from a pool on Base. No wrapped tokens appear; instead, the router’s internal accounting adjusts who is owed what across networks. This model can be more capital‑efficient and fast, but it depends heavily on the protocol’s liquidity depth and risk management. Slippage and temporary pool imbalances become important factors, especially during volatile market conditions or large flows.
—
Cross‑chain bridge fees and security: what you really pay for
When a new user compares cross‑chain options, they often focus on the obvious number: how many dollars of fees a given transfer costs. In reality, cross chain bridge fees and security are two ends of the same rope. More robust systems usually replicate more data on‑chain, maintain larger, better‑incentivized validator sets, and invest heavily in audits and bug bounties; all that operational work is partially baked into the price you pay per transaction. On high‑gas networks like Ethereum mainnet, just verifying proofs for a light‑client‑based bridge can add several dollars to each transfer, which is why rollups and cheaper L1s remain popular for everyday use.
At the same time, “cheap” is not always a good sign. When a bridge charges near‑zero fees without a clear monetization or security model, ask yourself who is subsidizing this and why. Sustainable systems usually collect a transparent protocol fee (for example 0.01–0.1% of volume) used for operations, security programs and, in some cases, slashing or insurance funds. In 2025, some advanced protocols also support configurable security tiers: you might pay a higher fee for a “high‑assurance” route that uses multiple verification layers and longer finality, or opt into a cheaper, faster path for lower‑value transactions. From a user perspective, the smart move is to look at total cost of ownership, including potential risk of loss, not just gas plus bridge fee.
—
Real‑world use cases: beyond just moving coins
Interoperability in 2025 is increasingly about applications that treat multiple chains as one environment. For example, a DeFi protocol might hold collateral on Ethereum but let you borrow and trade on a high‑throughput chain like Solana or a fast rollup. Cross‑chain DEX aggregators already route trades across multiple networks, searching for the best prices and liquidity, then settle your final position where you want to keep it. Gaming projects deploy logic on cheap L2s but settle rare NFT ownership or high‑value in‑game assets back to Ethereum mainnet, so that players get low‑fee gameplay with strong final ownership guarantees.
Another growing area is institutional and enterprise adoption. In 2025, several banks and fintechs experiment with tokenized deposits or real‑world assets that move across permissioned and public chains via standardized messaging. They use cross‑chain systems to synchronize balances, enforce compliance rules, and manage collateral in near real time. From the user standpoint this might look like a simple “send stablecoin to another chain” button in a mobile app, but underneath it uses the same interoperability primitives as DeFi. This convergence is one of the key modern trends: the same infrastructure that moves memecoins between rollups is quietly powering serious financial plumbing behind the scenes.
—
Trends to watch: modular stacks, restaking, and safer UX
Looking at 2025 and beyond, three big trends stand out. First, modular blockchains: instead of monolithic chains doing everything, we see specialized layers for execution, data availability, settlement and security. Interoperability becomes the glue that ties all these layers into something that feels like one chain from the user’s perspective. Rollups publish data to shared DA layers like Celestia, EigenDA or Avail, use Ethereum or other hubs for settlement, and still interact with each other via cross‑chain messaging.
Second, restaking and shared security are reshaping the risk profile. Instead of every bridge inventing its own token and security model, protocols can plug into restaked ETH, ATOM, or other major collateral pools, inheriting their economic weight. This does not magically remove risk, but it aligns incentives much better than thinly traded governance tokens that collapse during stress.
Third, UX is finally catching up. Wallets and frontends are slowly hiding chain boundaries: you choose what you want to do, and the app figures out where it should happen. Under the hood, it still matters which interoperability stack they use, but end‑users will see fewer confusing prompts, fewer manual network switches, and more human‑readable explanations. This is also where people increasingly look for cross chain interoperability solutions comparison built into wallets themselves, not just in blog posts or research reports. Ideally, your wallet becomes a “risk‑aware router” that picks safer options by default and clearly labels anything more experimental.
—
Choosing bridges in 2025: practical checklist for beginners
With so many options, it is easy to feel lost. Instead of chasing every new protocol, use a simple mental checklist when evaluating what might be the best cross chain bridges for beginners at any given moment. First, prioritize solutions that are widely integrated: if top wallets, blue‑chip DeFi apps, and major exchanges support a bridge, it has likely undergone more scrutiny than a random new site. Second, check security posture: reputable audits, public incident history, bug bounties, and clear explanations of what happens if something goes wrong. Third, look at volumes and liquidity; if daily volume is tiny and the TVL is low, large transfers may face slippage or delays.
Also consider how often the protocol gets updated and how transparent the team is about changes. In 2025, many mature cross‑chain systems publish real‑time dashboards with metrics like validator participation, message latency and chain‑specific risks. If a protocol hides behind vague marketing talk and does not show numbers, that is a good reason to be cautious. Finally, always align your tool with your purpose: an explorer or speculative strategy might justify trying newer, riskier tech with small amounts, while payroll, savings or business funds should stick to the most conservative cross‑chain routes available, even if they cost a bit more and take a little longer.
—
Wrapping up: what “multichain” really means for you
By 2025, “multichain” is no longer just a slogan on project websites. Underneath the hood, a thick layer of interoperability protocols, restaking systems, and standard messaging layers is turning a messy archipelago of chains into something that behaves more like a single, modular computing platform. For you as a beginner, that means two things. First, you do not have to master every technical detail before making a cross‑chain transfer, but understanding the basic models and trade‑offs will help you avoid the worst mistakes. Second, the best user experience happens when you let reputable wallets and dApps handle the heavy lifting, while you stay mindful of what you are approving, which protocol stands behind it, and how much you are willing to risk.
If you keep those principles in mind, cross‑chain stops being a scary maze and becomes just another everyday tool — like switching Wi‑Fi networks on your phone. The tech will keep evolving, with new security models and standards emerging, but the core goal stays the same: let value and information flow freely between chains while keeping your assets as safe as the most secure networks in the ecosystem.

