Cryptocurrency privacy in 2025 is no longer a niche obsession. With on-chain analytics, AI-based surveillance, and aggressive KYC rules everywhere, even regular users are starting to ask a simple question: “How do I pay, save, and move value without broadcasting my life to the entire internet?”
Below is a practical, up‑to‑date guide to building a privacy-preserving crypto workflow for daily use – from definitions to concrete setups you can actually follow.
—
Why a “workflow”, not just a “wallet”
A single “private wallet” is not enough anymore.
Exchanges log data, blockchains are permanent, your browser leaks metadata, and your phone is a walking tracking device.
Workflow here means the full chain of actions:
> From “I get some crypto” → to “I store and move it” → to “I spend it” → to “I cash out (if needed)”
> …with minimal personal trace at each step.
Think of it as a pipeline, not a single tool.
—
Key privacy concepts (without the jargon fog)
What “privacy” actually means in crypto
Let’s nail a few definitions that appear all the time in 2025 discussions:
– Pseudonymous – Addresses aren’t tied to your real name on-chain, but can often be linked to you via exchanges, IP logs, habits, and public leaks.
– Anonymous – Your transactions cannot be reasonably linked to your identity, even with external data. In practice, this is a spectrum, not a binary state.
– On-chain linkability – How easy it is to connect different addresses and payments as belonging to the same person or cluster.
– Transaction graph – The big map of money flows that blockchain analytics companies build. They don’t look at a single transaction; they look at *patterns*.
Modern privacy is about making this transaction graph as useless as possible against you.
—
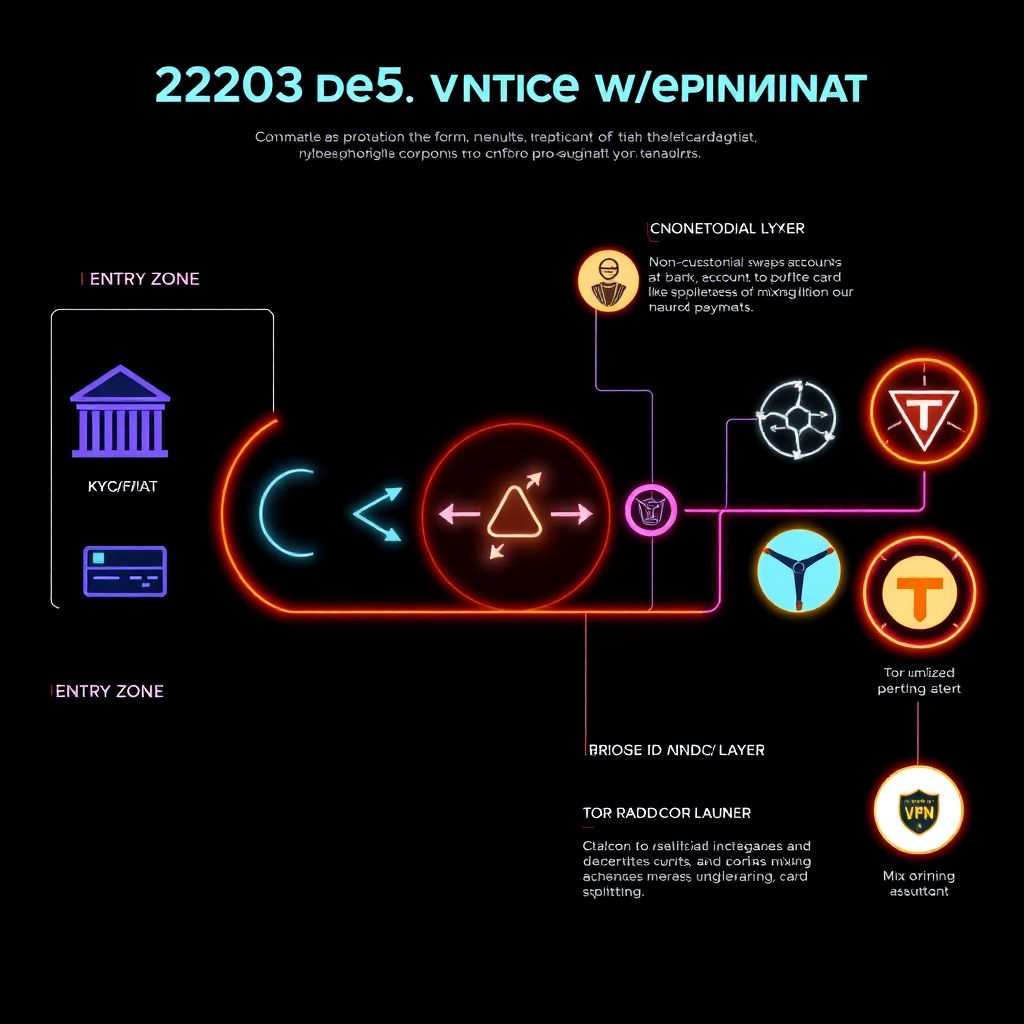
High-level architecture of a private workflow
Imagine a simple text diagram of a privacy‑oriented daily‑use setup:
1. Entry Zone (KYC/Fiat side)
– Salary, card payments, traditional banks, KYC exchanges.
– This is your “contaminated” zone.
2. Bridge / Anonymization Layer
– Swaps, coins that break links, mixing, privacy-preserving DEXes.
3. Private Spending Zone
– Privacy coins, hardened wallets, local or mobile setups used for actual day‑to‑day payments.
4. Exit Zone (if needed)
– Off-ramps back to fiat or KYC platforms, handled carefully and rarely.
You want:
> KYC world ←→ (thin bridge) ←→ private world
The trick is to make the bridge minimal, non-repeating, and hard to link.
—
Modern threats in 2025 you can’t ignore
What changed since the early bull markets
In 2025, the threat landscape is very different from 2017 or even 2021:
– AI-powered blockchain analytics
Companies now combine:
– On-chain data
– IP records from RPC nodes and explorers
– KYC data leaks
– Social media patterns
…to build shockingly accurate identity graphs.
– Wallet fingerprinting
The way your wallet constructs transactions, fee patterns, and connection habits (Tor vs direct) becomes a signature. Even “privacy tools” can be fingerprinted if used carelessly.
– Regulation of privacy tools
Some private bitcoin mixing services for daily transactions have been shut down, sanctioned, or heavily monitored. This doesn’t make privacy illegal by definition, but you must be aware of your local laws and stay away from obvious honeypots.
So your crypto workflow for daily use must be privacy-aware by design, not patched later.
—
Step 1: Building the “public” side without doxxing yourself
You rarely can avoid KYC for everything. But you can limit the blast radius.
Separate “public” and “private” identities
Do:
– Use one or two KYC exchanges only for:
– Converting salary → crypto
– Occasional on-ramp/off-ramp
– Avoid using those KYC addresses for:
– Paying friends
– Donations
– Anything sensitive
Don’t:
– Reuse a KYC deposit address as your main “crypto identity”.
– Post your KYC-linked address on social media or forums.
Think of KYC accounts as radioactive: touch them as little as possible, and only with gloves.
—
Step 2: Buying crypto with reduced traceability
How to anonymously buy crypto with no kyc (realistically)
In 2025, fully anonymous on-ramping is harder, but not dead:
– Peer-to-peer marketplaces
Some P2P platforms still allow non-KYC trades with limits. Combine them with:
– A hardened browser (Firefox with privacy add‑ons or Brave with shields)
– VPN + Tor (or Tor over VPN if you know what you’re doing)
– Cash-based local trades
In‑person deals or ATMs that don’t require KYC below certain limits.
Make sure:
– You don’t reuse the same phone number or email.
– You meet in a safe location, ideally public, with no cameras directly watching your screen or QR codes.
Remember: “No KYC” on the platform side doesn’t automatically mean anonymous. Payment rails, your IP, or your device fingerprint can still leak who you are.
—
Step 3: Using privacy coins as your daily “cash”
Why privacy coins are the new daily driver
For everyday payments, constantly fighting Bitcoin traceability feels like swimming upstream. That’s why a guide to using monero and privacy coins for daily payments has become a core part of modern privacy workflows.
Monero, Firo, and a few others:
– Hide sender, receiver, and amount (by default).
– Have active ecosystems for merchant tools, wallets, and swaps.
– Provide default privacy, not opt‑in.
Practical Monero-focused daily workflow
A typical pattern:
1. Convert BTC/ETH/USDT → XMR via a non‑custodial swap (ideally no KYC, Tor-friendly).
2. Hold XMR in a mobile wallet with strong security.
3. Pay:
– Directly in XMR where supported.
– Via instant swaps: XMR → merchant’s coin via atomic or bridge swaps.
Example:
You’re paying a freelance designer. They accept USDT, BTC, and XMR.
– You keep your funds mostly in XMR.
– When you need to pay, you:
– Swap XMR → USDT using a Tor-connected, non-custodial swap service, then.
– Send USDT to their given address.
From an outside observer’s view, most of your activity sits in the Monero ecosystem, which is opaque by default.
—
Step 4: Private use of Bitcoin (if you still need BTC)
What’s realistically possible with Bitcoin privacy in 2025
Bitcoin isn’t built for anonymity, but it can be used more privately with some discipline.
Core techniques now:
– Coinjoin-style protocols (where legal)
Used to break linkability of coins linked to KYC or public addresses.
– Collaborative transactions & PayJoin
Two parties create a transaction together to confuse who’s paying whom.
– UTXO management
Tracking and tagging “dirty” vs “clean” coins, and not mixing them.
This is where private bitcoin mixing services for daily transactions historically came in. In 2025:
– Many centralized mixers are either:
– Shut down;
– Under surveillance;
– Obvious traps.
Prefer tools that are:
– Non-custodial – you never hand over full control.
– Open-source – the code can be audited.
– Decentralized or collaborative – no single “operator” that can log everything.
Always combine Bitcoin privacy tools with:
– Tor-only connections.
– Wallets that support coin control and labeling.
– Strict rule: never send mixed coins back into the same KYC exchange that gave you the original coins.
—
Step 5: Choosing and structuring your wallets
What a “secure crypto portfolio setup for privacy focused users” looks like
Instead of one giant wallet, break things into roles. Here’s a text diagram:
– Cold Vault (Long-term savings)
– Hardware wallet or air-gapped device
– Multi-coin, minimal internet contact
– Used rarely; addresses never shared publicly.
– Private Spending Wallet (Daily payments)
– Mobile or desktop wallet dedicated to privacy coins (e.g., Monero) and some BTC.
– Always routed over Tor or a reputable VPN.
– Used regularly but with limited balances.
– Bridge / Swap Wallet
– Temporary addresses to convert KYC → private (and back if needed).
– Coins kept only for short periods; this is your “DMZ”.
To find the best privacy crypto wallets for everyday use, focus less on marketing claims and more on:
– Do they support Tor, custom nodes, or your own RPC?
– Do they leak data to third-party analytics (e.g., automatic “portfolio tracking” features)?
– Can you easily separate multiple profiles or accounts?
—
Step 6: Metadata hygiene (where most people fail)

Even if your coins are private on-chain, you can still leak a ton of info via metadata.
Things that quietly deanonymize you
– Reusing the same device identity (mobile + SIM + Wi‑Fi) for both KYC app and private wallet.
– Always connecting from your home IP.
– Sharing screenshots or transaction hashes with visible timing and amounts.
– Logging into a central price‑tracking app that tracks every wallet address you input.
To improve your hygiene:
– Use:
– Separate profiles: one browser profile for “public/KYC” stuff, another for private.
– Network isolation: Tor/VPN for your private wallet; normal connection for regular browsing.
– Avoid:
– Linking emails, phone numbers, or IDs across private and public exchanges.
– Using cloud backups of seed phrases or wallet files.
Privacy here isn’t paranoia; it’s simply not handing free data to companies whose business is tracking you.
—
Step 7: Concrete example of a 2025 daily privacy workflow
Let’s build a realistic scenario.
Situation
– You get paid monthly into a KYC exchange in USDT.
– You want:
– Long-term BTC and XMR savings.
– Daily XMR spending.
– Occasional card/top-up for fiat expenses.
Workflow outline
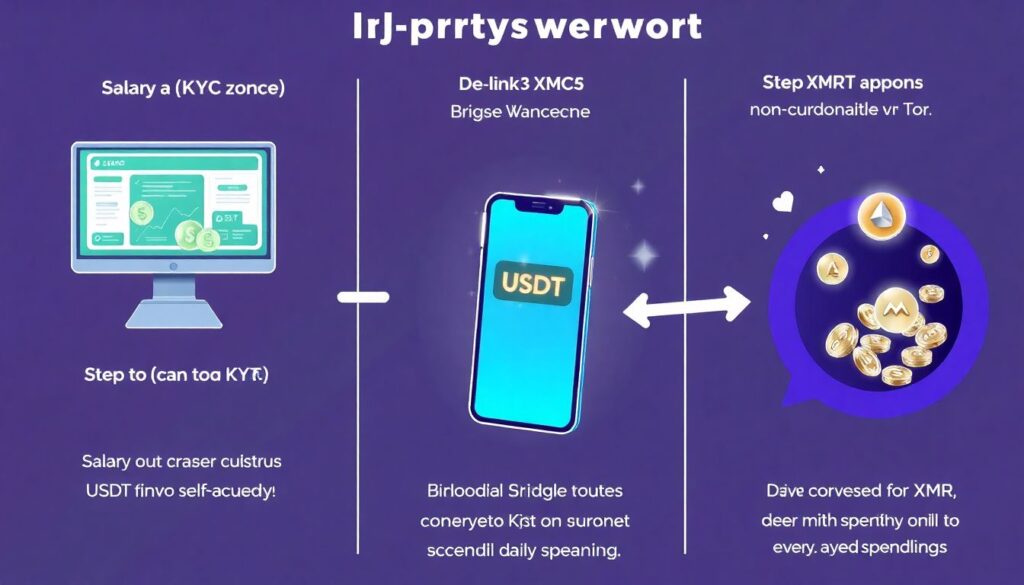
1. Salary arrives (KYC zone)
– USDT lands on KYC exchange.
2. Move to self-custody
– Withdraw USDT to a fresh address in your Bridge Wallet.
3. De-link from KYC
– From Bridge Wallet, use a non-KYC swap (over Tor) to:
– Convert a portion USDT → XMR (for daily spending).
– Convert some USDT → BTC, then run through a non-custodial coinjoin or collaborative tool, then send to Vault Wallet.
4. Everyday use
– Keep a modest XMR balance in your Private Spending Wallet (mobile or lightweight desktop).
– Make daily payments directly in XMR where possible or swap XMR → merchant coin on-demand via Tor.
5. Occasional cash-out
– When you need fiat:
– Move a small amount from private coins → BTC or USDT via private swap.
– Send to KYC exchange or a card provider.
– Withdraw to bank or card, respecting local regulations and keeping patterns irregular.
This setup is not “perfect anonymity”, but it drastically reduces obvious links and creates a usable, repeatable habit.
—
Comparing privacy workflows: Bitcoin only vs Privacy coins hybrid
Pure Bitcoin approach
– Pros:
– One asset to manage.
– High liquidity, easy off-ramps.
– Cons:
– Constant fight with linkability.
– Tools are increasingly scrutinized and sometimes blacklisted.
– Harder to maintain strong privacy over many daily transactions.
Hybrid with Monero or other privacy coins
– Pros:
– Default privacy for day‑to‑day payments.
– Bitcoin used mainly as a long‑term savings and liquidity asset.
– Simpler mental model: “BTC/XMR for savings, XMR for spending”.
– Cons:
– Need to manage swaps and possibly more wallets.
– Some exchanges and jurisdictions are suspicious of privacy coins.
In 2025, most serious privacy users end up with some version of the hybrid model.
—
Practical checklists to stay sane
Quick reality check for your setup
Ask yourself:
– Can someone easily see my salary and daily spending on a block explorer?
– Am I reusing addresses from KYC for personal or sensitive payments?
– Is my “private” wallet running from the same IP and device as my KYC app?
If the answer is “yes” to any of these, your workflow needs tuning.
Minimal “to-do” list for better daily privacy

– Separate:
– KYC exchange identity
– Bridge wallet
– Private daily wallet
– Cold storage
– Use:
– Privacy coins for daily payments where possible
– Tor or at least a reputable VPN for your privacy tools
– Non-custodial swaps instead of centralized, opaque services
– Avoid:
– Posting your addresses publicly
– Using the same wallet for friends, merchants, and savings
– Blindly trusting browser extensions with your keys and metadata
—
Final thoughts: Treat privacy as a habit, not a stunt
A privacy-preserving crypto workflow for daily use in 2025 isn’t about a single magic app. It’s about:
– Separation (KYC vs private).
– Default private medium (usually Monero or similar).
– Good hygiene (network, devices, and behavior).
– Occasional, careful bridges to/from the fiat world.
Start small: split your wallets, introduce a privacy coin for some everyday payments, and slowly harden your setup. The goal isn’t to disappear from the planet; it’s to stop making your financial life a public data feed for whoever feels like watching.