Why crypto security feels so weird (and why you should care)
If you lose your bank password, you click “reset” and yell at support if something goes wrong. If you lose your seed phrase, there is no support line, no chargeback, no legal department to lean on. That’s why crypto security feels more like running a small, high‑value server than using a finance app. Understanding crypto security best practices is basically understanding how to be your own mini‑bank: you control the keys, you control the backups, you control the devices, and any mistake can be final. The good news is that with a bit of structure, you can have strong security without turning your life into a paranoid thriller. The goal is to build a setup that you will actually maintain over years, not just something that sounds hardcore on Reddit.
—
Threat model 101: what are you actually defending against?
Before arguing about wallets and backups, get clear on your threat model. In plain terms, who might want your coins, and how would they try to get them? For most people, the realistic attackers are: malware on your laptop or phone, phishing websites, compromised browser extensions, and cloud leaks where screenshots or seed phrases accidentally end up in Google Drive or iCloud. If you’re a public figure or hold a visible NFT collection, add targeted social engineering and SIM-swaps to that list. Physical threats like break‑ins or “wrench attacks” (someone forces you to unlock a wallet) are rare but not imaginary. Once you map this out, the rest of your setup—how to securely store cryptocurrency, where to keep backups, which devices to trust—starts to look like a series of trade‑offs instead of random paranoia.
—
Storage approaches: cold, warm, and hot, explained like a human
Let’s slice storage options into three buckets: hot, warm, and cold. Hot wallets live on internet‑connected devices—browser extensions, mobile wallets—great for daily use but exposed to every bug and phishing attempt that hits your device. Warm storage is usually a hardware wallet used regularly but kept nearby, sometimes plugged in, sometimes not. Cold storage means keys that never touch an online system: a hardware wallet locked away and only connected rarely, or even an air‑gapped device used just to sign transactions. The trick is to avoid a single all‑in‑one wallet that does everything. Treat hot wallets like a checking account with limited funds, and treat cold setups like a long‑term vault you almost never open.
—
hardware wallet vs software wallet security: what actually matters
People obsess over brands, but the real question in hardware wallet vs software wallet security is where your private key is exposed. Software wallets keep your key in device memory or secure enclaves; that’s only as strong as the operating system, your update habits, and whether malware is present. Hardware wallets keep keys inside a dedicated chip and sign transactions internally, so the key never leaves that secure element. This does not make them magic—if you approve a malicious transaction on a compromised computer, the hardware wallet will happily sign the wrong thing. For most non‑trivial amounts, a hardware wallet plus a dumb, locked‑down laptop used only for crypto already puts you far ahead of casual attackers and drive‑by malware.
—
Multisig, passphrases and social recovery: not just for whales
Advanced setups like multisig sound like overkill, but they’re becoming practical even for regular users who want to be serious about protecting crypto from hackers and accidents. Multisig lets you spread signing authority across devices or even people: for example, a 2‑of‑3 scheme across two hardware wallets and one mobile wallet. A passphrase (sometimes called the “25th word”) layered on top of your seed transforms a stolen backup into useless gibberish, as long as you can remember or securely store that extra secret. Social recovery wallets and smart‑contract based setups add another twist: you appoint “guardians” (devices or trusted contacts) that can help you recover keys if you lose them, without having a single piece of paper that, if photographed, wrecks your life. The catch is complexity: these schemes must be documented and tested, or you risk locking yourself out instead of attackers.
—
Backups: more important than the wallet itself
Most people worry about hackers and forget the more boring threat: their own future self. Disks fail, flats burn, relationships end, memory fades. Your secure crypto backup solutions have to survive all of that while staying useless to anyone who finds them. At a minimum, you want at least two geographically separated backups of your seed or recovery setup, protected from both physical destruction and casual discovery. This can mean a fireproof safe in your home plus a safe‑deposit box, or a trusted legal office holding sealed envelopes under a contract. The key is that losing one location, one device, or one piece of paper should never equal total loss of funds. And whatever you choose, you must periodically verify that you can restore from backup on a fresh device without bugs or missing pieces.
—
Non‑standard (but practical) backup ideas
Paper and metal seed plates are fine, but let’s talk more creative options. One approach is a split‑knowledge backup: you cut your seed into two or three parts (or use Shamir’s Secret Sharing) and store them in separate places, requiring a subset to reconstruct. That way, a burglar who finds one piece still gets nothing. Another more unusual method is to wrap your seed in a password‑protected archive that uses strong, modern encryption (for example, age or modern GPG curves) and store it across multiple cloud providers under innocuous names—essentially treating the internet as a redundant, encrypted dead‑drop. You can even combine both: encrypted seed plus Shamir split, so any cloud leak is just scrambled math. The non‑negotiable rule is to test recovery: create a test wallet, back it up with your fancy scheme, then restore it from scratch and send funds back and forth to prove it really works.
—
Device hygiene: your keys are only as clean as your hardware
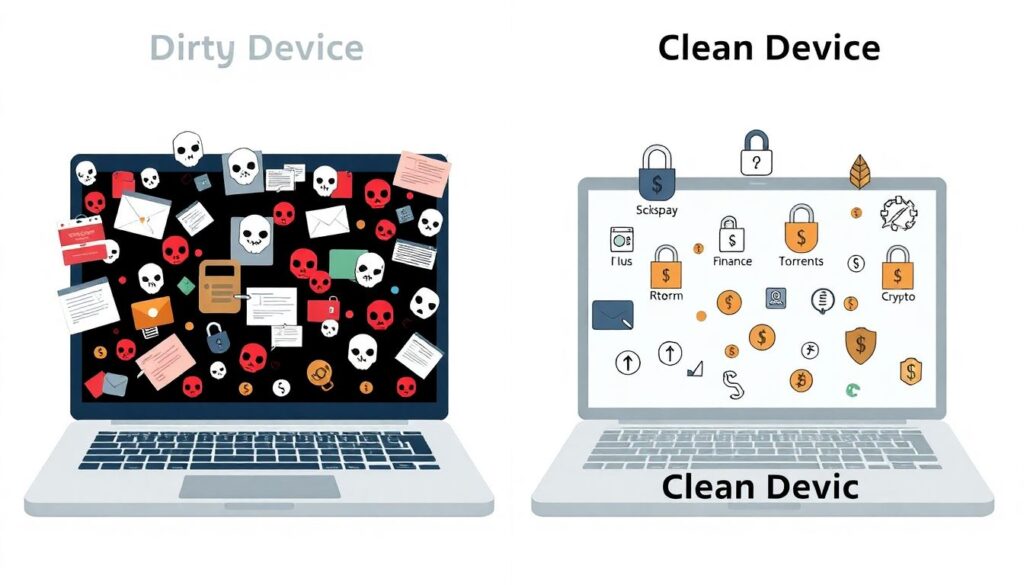
Even the best wallet fails if the computer you plug it into is a malware zoo. Device hygiene is simply applying basic infosec discipline to your daily tech. Start by separating roles: use one “dirty” device for browsing, torrents, random apps, and another “clean” device reserved for finance and crypto. The clean device should have full‑disk encryption, a non‑admin daily user account, minimal software installed, and automatic OS security updates enabled. Disable browser plugins you don’t absolutely need, especially anything that reads or writes to pages where you sign transactions. Keep strong device unlock codes—no four‑digit PINs—and avoid leaving machines unattended and unlocked in public spaces or shared offices. This isn’t about being fearless; it’s about reducing the attack surface so that a single dumb click on a link doesn’t turn into a wallet drain.
—
Mobile and desktop practices that actually move the needle
On mobile, uninstall any wallet you don’t actively use, and switch off automatic installation of unknown .apk packages. Lock down notifications on your lock screen; sensitive codes or wallet alerts that pop up there can leak context to shoulder‑surfers. On desktops, remove pirated software and dodgy browser extensions—both are prime malware vectors. Never copy your seed phrase into a password manager or notes app, even if encrypted; those apps are big, juicy targets. Instead, use them for less critical secrets like exchange passwords and 2FA backup codes. Whenever possible, use a hardware security key (FIDO2) for exchange logins, and avoid SMS‑based 2FA that’s vulnerable to SIM‑swap attacks. This combination—a clean OS, limited software, hardware‑based logins—dramatically lowers the chances that a random drive‑by exploit escalates into a full compromise of your wallet environment.
—
Choosing your setup: a practical decision tree

To avoid drowning in options, treat your choices as a series of simple questions. Answer them honestly, and you’ll end up with a custom plan instead of copying someone else’s extreme configuration. Think of it as designing a system that balances friction and safety for your actual life, not some anonymous crypto whale on X.
- How much is at stake, realistically, in fiat terms? Adjust ambition accordingly; you don’t need a five‑layer multisig for $200, but you also shouldn’t trust a hot browser wallet with your life savings.
- How often do you transact? Frequent DeFi users benefit from a dedicated hot wallet with strict limits plus a deeper cold vault; long‑term holders can bias heavily toward cold storage with rare, deliberate movements.
- Who are your plausible attackers? If you’re mostly worried about random malware, focus on device hygiene and a hardware wallet. If you fear physical threats or local coercion, add multisig across locations or a plausible‑deniability wallet with smaller balances.
- How good are you at not losing things? Be honest. If you misplace everything, complex backup schemes might backfire; you may want social recovery, legal custodians, or a hybrid solution instead of a single metal plate in your drawer.
- Will anyone need access if something happens to you? Plan inheritance explicitly—document a recovery path in a sealed letter or legal will, assuming your future self is unavailable to explain anything.
When you work through these, the question is no longer abstract how to securely store cryptocurrency; it becomes “which specific mix of wallets, backups, and devices fits my life and risk level.”
—
Current trends and near‑future directions for 2025
Security patterns around crypto are changing quickly as the ecosystem matures. We’re seeing a clear shift toward smart‑contract based wallets with built‑in spending limits, session keys for dapps, and configurable social recovery, which reduces the damage a single lost device can cause. More hardware wallets now integrate secure elements, open‑source firmware, and verifiable builds, narrowing the gap between consumer gadgets and traditional HSMs. On the backup side, user‑friendly Shamir implementations and guided onboarding are turning previously niche schemes into mainstream secure crypto backup solutions for high‑value users. Regulators and enterprises are also pushing better auditing of wallet code and supply chains, which in turn nudges retail users toward vetted products rather than random closed‑source apps. Overall, the direction of travel is away from raw seed phrases on paper and toward built‑in guardrails that make catastrophic loss harder by design.
—
Non‑obvious tactics to quietly harden your setup
Beyond the standard playbook, there are a few underused tricks that offer big security wins with modest hassle. One is to create a “decoy tier” of holdings: a small but non‑trivial amount kept in a simpler, more visible wallet. If you’re ever pressured in person, that wallet gives you something to unlock without exposing your true cold storage. Another is to maintain a small, sacrificial hot wallet used exclusively for connecting to experimental dapps and new chains; if something goes wrong, the worst‑case loss is limited by design. You can even run a low‑cost, always‑on mini‑PC or single‑board computer as a dedicated signing station: no browsing, no email, just wallet software and updates, effectively a “poor man’s HSM” for home users. Combine those with consistent device hygiene and you end up with a layered architecture that makes protecting crypto from hackers far less fragile than a single key and a single backup in a single drawer.
—
Wrapping up: security as a habit, not a one‑time setup
Crypto security isn’t about buying one magical gadget or memorizing one obscure protocol; it’s about building habits and structures that tolerate your future mistakes. Your plan needs three pillars: a hardened storage strategy that separates hot and cold funds, backups that survive both fires and forgetfulness, and devices that are boringly clean instead of chaotic. Revisit your setup at least once a year: confirm you can still restore from backup, check whether your threat model has changed, and prune old apps or wallets that no longer serve a purpose. If you treat your wallet stack the way an engineer treats production systems—assume failure, design for redundancy, and test recovery—you’ll be in far better shape than most of the market, without needing to live in a bunker or become a full‑time security researcher.