Introduction to cross‑chain token bridges
Why bridges exist
In 2025 the crypto landscape is unavoidably multi‑chain. You have Bitcoin, Ethereum, L2 rollups, Solana, Cosmos zones, app‑chains, sidechains – none of them talk to each other natively. Cross‑chain token bridges try to stitch this ecosystem together so that capital can move where it’s needed: to cheaper fees, better yield, or a specific dApp. At a high level, a bridge is middleware that lets you lock assets on one chain and gain equivalent economic exposure on another. Without this layer, liquidity would be fragmented, DeFi yields would be lower, and many “omnichain” apps simply couldn’t exist. That said, every additional connection between chains is also an additional attack surface, which is why regulators, developers and sophisticated users track bridge exploits almost as closely as they track prices.
Bridges trade convenience for complexity. Once you leave a single chain, you’re no longer trusting only its base consensus; you’re trusting extra code, external validators, and sometimes off‑chain infrastructure.
Basic architecture in plain terms
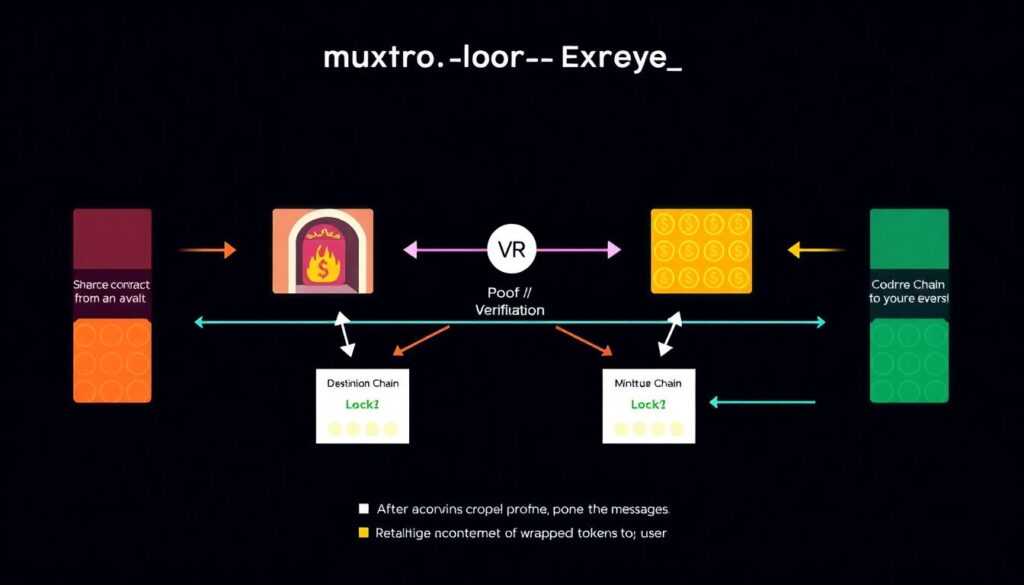
Most cross‑chain bridges follow the same conceptual pattern. On the source chain, a smart contract receives your tokens and either locks or burns them. Some proving mechanism then convinces a contract on the destination chain that this lock really happened. Finally, that destination contract mints or unlocks a corresponding asset for you. The “magic” is entirely in how the proof moves across: it might be an off‑chain relayer, a validator committee, or a light client that verifies another chain’s headers. Each design optimizes for a different trade‑off between cost, latency and security. When you look for the best cross-chain bridge for crypto, what you’re really comparing is not only UX and fees, but the underlying trust assumptions built into this architecture.
How cross‑chain bridges work in practice
Lock‑and‑mint model
The dominant design is the lock‑and‑mint, sometimes called “wrapped asset” bridges. Suppose you send ETH from Ethereum to a sidechain. The bridge contract on Ethereum locks your ETH in a vault that ideally nobody can touch directly. Then, on the sidechain, the bridge contract mints wrapped ETH, a synthetic token that tracks the value of the locked ETH. When you go back, the wrapped token is burned and the original ETH is released. In many 2020–2024 hacks, attackers found ways to trick the destination contract into minting more wrapped tokens than there were locked originals. This is why cross-chain bridge security risks are so dangerous: one logic bug can instantly create unbacked assets and drain real collateral, even if the underlying L1 is perfectly secure and functioning.
An important implication: you’re never literally “moving” your original coins across chains; you’re swapping base‑layer security for bridge‑layer security.
Liquidity network and router models
The other big model doesn’t rely on locking and minting, but on liquidity providers. Systems like “routers” or “liquidity networks” maintain token pools on multiple chains. When you bridge, you’re basically trading your token on chain A for tokens from that pool on chain B. Under the hood, professional market makers and bots rebalance inventory and charge fees to keep everything in line. This approach can be capital‑intensive but avoids a giant honeypot of locked assets. From a beginner’s point of view, it still looks like a single “bridge”, but the risk profile is different: instead of a huge vault contract, your main risks are pool insolvency, mis‑priced oracles, and protocol‑level governance failures. For many users, this can be a safer way to bridge crypto assets, especially when the protocol is transparent about how it handles LP funds and slippage.
Routers feel more like using an on‑chain exchange that happens to span multiple networks than a classic custodial tunnel.
What the user actually does: workflow
Let’s walk through how to transfer tokens between blockchains with a typical web interface. You connect a wallet like MetaMask, pick a source chain, a destination chain and the token. The UI estimates the fee, route and expected arrival time, then you approve the token and confirm the bridge transaction. After some confirmations on the source chain and verification through the bridge mechanism, your wrapped or bridged asset appears on the destination chain. From your perspective, it’s a two‑click process; under the hood, there might be multi‑sig validators signing messages, relayers paying gas on your behalf, or zk‑proofs verifying block headers. Beginners often underestimate that this apparently simple step involves multiple off‑chain services staying honest and online. Any failure—relayer downtime, validator collusion, or a bug in serialization—can freeze funds or delay them for days.
If something looks “instant” and cheap, you’re probably paying with extra trust rather than with gas fees.
Key risks and notable incidents
Technical attack vectors
Statistically, bridges have been among the biggest security sinkholes in crypto. Between 2021 and 2024, public datasets from firms like Chainalysis and TRM Labs attribute roughly 50–60% of all DeFi funds stolen in major incidents to cross‑chain bridges, with single hacks exceeding $600M. The technical paths vary: key compromise of validator multisigs, bugs in light‑client verification, integer overflows, replay attacks and poorly designed upgrade mechanisms. Because bridges sit at the boundary between chains, their contracts are often more complex than typical DeFi apps, and they have to parse messages from heterogeneous environments. Attackers love this complexity. Once they can convince the destination side that a non‑existent lock occurred, they can mint arbitrary tokens, cash out through DEXs, and leave users with unbacked IOUs that look real until liquidity disappears.
Even formally verified contracts can be undermined by misconfigured signers or insecure devops practices.
Economic and governance risks
Not all failures show up as spectacular hacks. Some play out as slow‑burn economic issues or governance mistakes. For example, if a bridge relies on a small set of validators, then economically it functions like a semi‑custodial bank. Those operators can be bribed, regulated, or simply turn rogue. In bear markets, when volumes shrink, incentives to keep nodes running and secure may weaken, raising latent risk. Another subtle risk is de‑pegging: if a wrapped token falls out of favor or the bridge governing it loses community trust, markets may start trading that asset at a discount. Holders who thought they had 1:1 exposure realize they’re effectively holding a risky corporate IOU. For DAOs, concentrating treasury assets in a single bridge magnifies systemic risk: if that bridge fails, not only do they lose funds, but liquidity and governance power on the destination chain can evaporate overnight.
From an economics standpoint, bridge risk is a combination of smart‑contract risk, counterparty risk, and liquidity risk, all rolled into one.
Statistics and market landscape in 2025
Volumes and growth
By early 2025, cross‑chain bridges routinely process tens of billions of dollars in monthly volume across the top ecosystems. Aggregated dashboards show that a handful of leading protocols dominate, with Ethereum–L2 and Ethereum–Solana corridors carrying the lion’s share. After each major hack between 2021 and 2023, volumes temporarily dropped 20–40%, but rebounded as new versions shipped with improved validation schemes, bug‑bounty programs and insurance modules. Analysts now estimate that over 30% of total DeFi TVL touches a bridge at some point in its lifecycle, either via direct transfers or via protocols that rely on bridged collateral. This means the overall health of DeFi is tightly coupled to how robust these cross‑chain connectors are. If a systemic bridge fails, the shockwaves can propagate into lending markets, derivatives, and even NFT pricing as forced liquidations cascade through multiple chains.
Bridge metrics are now a staple in institutional risk dashboards, alongside stablecoin reserves and exchange solvency indicators.
Concentration and centralization

A concerning pattern in 2025 data is concentration: a small cluster of bridging protocols, often backed by the same large funds and market makers, controls a majority of inter‑chain liquidity. This raises familiar “too big to fail” worries. If the de facto best cross-chain bridge for crypto in terms of UX and liquidity is also highly centralized, the ecosystem drifts away from the trust‑minimized ethos that attracted many early users. However, there’s an emerging counter‑trend: app‑specific bridges baked directly into rollups or interconnected within ecosystems like Cosmos and Polkadot. These designs reduce dependency on third‑party validators and rely more on native interoperability features. For beginners, this fragmentation is confusing—there might be three or four different routes between the same two chains, each with its own fee model and risk profile. But from a systemic viewpoint, diversity of bridges acts as a resilience mechanism if one major connector goes down.
We’re gradually moving from “one giant bridge per corridor” to overlapping, specialized routes that share less correlated failure modes.
Evaluating security and choosing a bridge
Due‑diligence checklist in human language
When you pick a secure cross-chain token bridge, think less about brand recognition and more about what you’re actually trusting. How many independent validators or oracles does it use, and who controls them? Is the code open‑source and audited by credible firms, with public reports? Does the protocol have a track record of handling incidents transparently, including halts and upgrades? On the economic side, what insurance, if any, exists for users in case of exploits? Some bridges maintain dedicated coverage funds or integrate with on‑chain insurance protocols. Latency and fees also matter, but for long‑term capital, security dominates. A practical heuristic for beginners: if a bridge is heavily used by serious DeFi protocols and referenced in governance discussions by blue‑chip DAOs, it’s at least passed some real‑world stress tests, though this is no guarantee of safety.
Blindly trusting flashy marketing or high APYs on bridged farms is a shortcut to becoming exit liquidity.
What “secure” actually looks like
From a more technical standpoint, a safer way to bridge crypto assets tends to minimize off‑chain trust and concentrated keys. Native light‑client bridges, which verify cryptographic proofs of another chain’s consensus, are closer to “trustless”, but they’re expensive and complex to build. Validator‑set bridges can be fine if the set is large, economically bonded and slashable for misbehavior. Multi‑sig setups with 5–10 signers, while common, are closer to federated custodians than to permissionless protocols. Future‑oriented designs are experimenting with zero‑knowledge proofs, optimistic validation and modular interoperability layers that chains can plug into. For a beginner, you don’t need to master all cryptography; you just need to recognize red flags: opaque ownership, missing audits, rushed token launches, unrealistic yields, and lack of clear documentation about failure procedures. A bridge that explains its limitations honestly is usually safer than one that markets itself as “unhackable”.
In practice, good security also includes boring things like rate‑limits, circuit breakers and staged rollouts rather than instant mainnet deployments.
Future outlook and development forecasts
Tech trends through 2030
Looking out from 2025, most serious researchers expect cross‑chain infrastructure to become more protocol‑level than app‑level. Instead of dozens of ad‑hoc bridges, we’ll likely see standardized interoperability layers embedded into L1s and rollups. This could push the current fragmented space toward a handful of open standards, somewhat like how TCP/IP unified networking. Cross‑chain bridge security risks should decline as more designs adopt formal verification, zk‑proof based light clients, and more robust cryptoeconomic incentives for validators. Industry analysts project that by 2030, over 60–70% of cross‑chain volume might flow through such “native” or semi‑native mechanisms, with traditional third‑party bridges handling niche corridors and legacy assets. That doesn’t mean risk disappears; each new abstraction hides complexity that attackers will probe, but the blast radius of single‑contract bugs should shrink.
We’re also likely to see better user‑facing insurance and standardized disclosures, similar to prospectuses in traditional finance.
Regulatory and industry impact
On the regulatory side, cross‑chain activity is already under the microscope because bridges often facilitate large, fast transfers that can evade simple chain‑specific monitoring. By 2025, multiple jurisdictions are pushing guidance that treats some centralized bridges almost like virtual asset service providers, with KYC and reporting duties. This will likely bifurcate the market: more compliant, institution‑friendly corridors for large capital, and more permissionless, censorship‑resistant rails favored by DeFi natives. For the broader crypto industry, robust interoperability is a prerequisite for mainstream adoption. Institutions don’t want to care which chain they’re on; they want reliable settlement and predictable risk. As bridges mature, the question shifts from “how to transfer tokens between blockchains at all” to “how to do it with clear SLAs, insurance, and well‑understood governance”. Projects that solve this reliably will underpin the next wave of cross‑chain applications, from unified DEXs to chain‑agnostic identity and gaming.
If you’re just starting now, learning how these systems work puts you ahead of where most users will be when cross‑chain becomes the default, not the exception.