Understanding the Core Risks in Crypto Asset Management

Before diving into protection strategies, it’s critical to analyze the unique vulnerabilities associated with crypto assets. Unlike traditional bank accounts, cryptocurrencies operate in a decentralized environment where users retain full custody. This autonomy is empowering, but it also means that any loss due to hacking, phishing, or key mismanagement is typically irreversible. The most prevalent threats include compromised private keys, malware attacks, phishing schemes, and custodial platform failures. A nuanced strategy must address both technological and behavioral risks, combining secure storage with informed decision-making.
Essential Tools for Protecting Digital Assets
Protecting crypto assets begins with selecting the right combination of tools. Hardware wallets, such as Ledger or Trezor, are foundational for cold storage—keeping private keys offline and mitigating exposure to online threats. Multi-signature wallets add another layer of security by requiring multiple approvals for transactions. For active traders, browser extensions like MetaMask should be paired with hardware wallets to reduce hot wallet exposure. Password managers, encrypted backups, and air-gapped devices also play a crucial role in minimizing human error and digital compromise. Using open-source tools with verifiable codebases enhances transparency and trust.
Step-by-Step: Building a Secure Crypto Asset Strategy
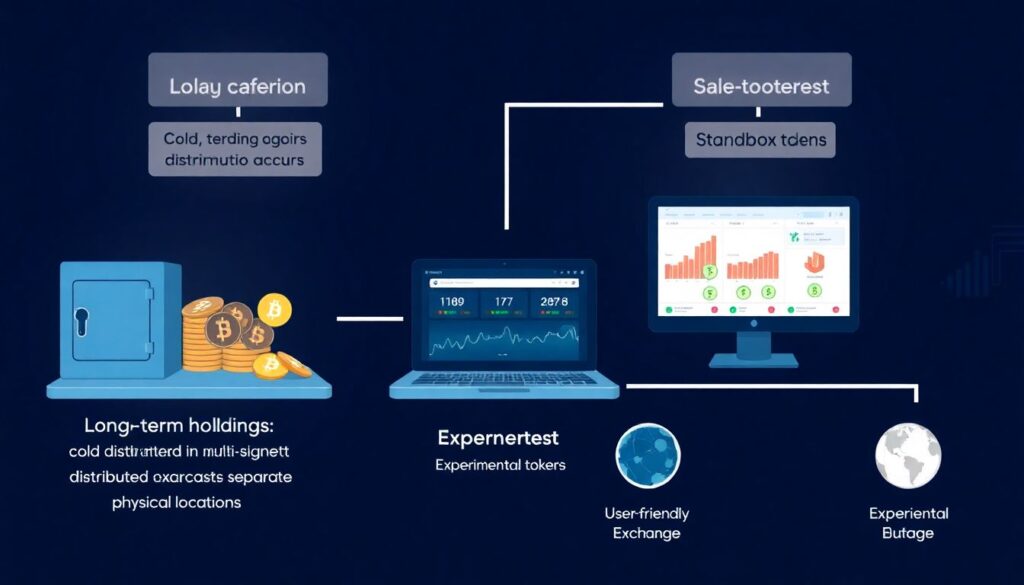
The first step is categorizing your assets by activity level—long-term holdings, active trading funds, and experimental tokens. Long-term holdings should reside in cold storage, preferably in a multi-signature configuration stored across separate physical locations. Active trading funds can remain in hot wallets but should be protected with two-factor authentication and biometric access. Avoid storing large sums on centralized exchanges. Next, implement a key management protocol: generate seed phrases offline, store them in tamper-evident envelopes or steel plates, and avoid cloud backups. Finally, conduct routine audits—review wallet access, revoke unnecessary permissions, and test recovery procedures.
Advanced Tactics: Beyond Traditional Security
To go beyond conventional methods, consider integrating decentralized identity (DID) systems to verify wallet ownership without exposing private credentials. Set up a crypto dead man’s switch using smart contracts, which can automatically transfer assets if you become inactive for a predefined time—useful for estate planning. Additionally, employ honeypot wallets with small balances to mislead attackers and monitor intrusion attempts. For institutional investors, adopting threshold signature schemes (TSS) offers similar benefits to multi-signature wallets but with greater efficiency and privacy. Periodically rotate keys and separate duties among trusted parties to reduce the risk of internal breaches.
Troubleshooting Common Security Pitfalls
Even with robust protocols, misconfigurations and oversights can compromise security. One frequent issue is seed phrase mismanagement—storing it digitally or failing to test recovery can lead to permanent loss. To troubleshoot, simulate wallet recovery on a separate device to ensure access. Another common problem is phishing attacks mimicking wallet interfaces or customer support. Always verify URLs and avoid clicking unknown links. If a suspected breach occurs, immediately transfer funds to a new secure wallet and revoke smart contract permissions via blockchain explorers. Staying updated on threat vectors and participating in security forums can also help identify and mitigate emerging risks.
Conclusion: Evolving with the Crypto Security Landscape
Crypto asset protection is not a one-time setup but an evolving discipline that must adapt to changing technologies and attack vectors. By combining technical safeguards with strategic planning, users can significantly reduce exposure to both external and internal threats. The key lies in proactive risk management—regular updates, diversified storage, and knowledge sharing. As decentralized finance and Web3 ecosystems expand, crypto security must transition from reactive defense to anticipatory resilience. Crafting a personalized, multi-layered protection strategy is no longer optional—it’s essential for anyone serious about safeguarding their digital wealth.