Introduction to Cross-Chain Bridges Security

Cross-chain bridges serve as critical infrastructure in the decentralized ecosystem, enabling interoperability between distinct blockchain networks. These protocols allow assets and data to move seamlessly across chains such as Ethereum, BNB Chain, Solana, and others. However, due to their complex architecture and reliance on external validators or smart contracts, bridges have become prominent targets for exploits. Understanding the security models of cross-chain bridges is essential for developers, investors, and users engaging in decentralized finance (DeFi) and multi-chain applications.
Comparison of Cross-Chain Bridge Architectures
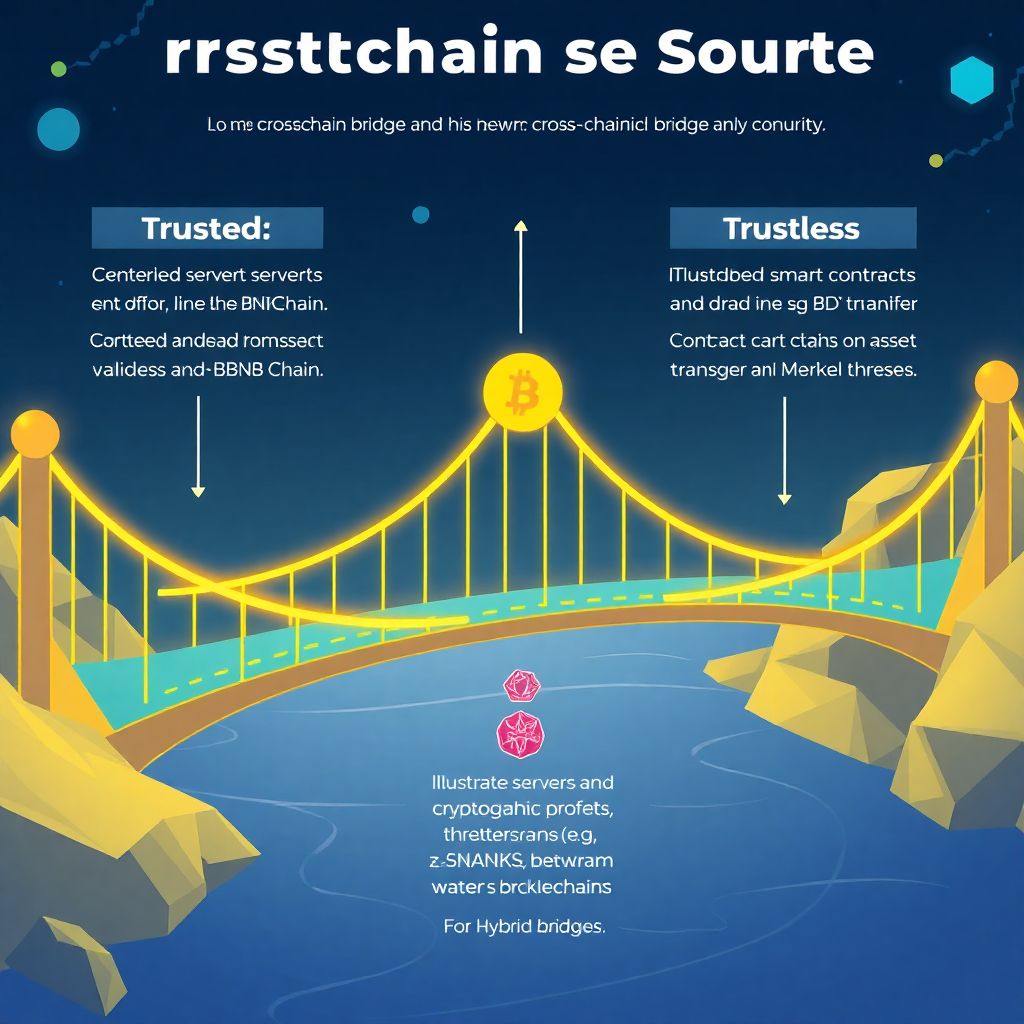
1. Trusted Bridges
Trusted bridges rely on a centralized or semi-centralized set of validators or a multi-signature wallet to verify and authorize transactions between chains. Examples include Binance Bridge and Polygon PoS Bridge. While these systems offer faster performance and lower costs, they introduce a central point of failure. If the validators are compromised or collude, the entire bridge is at risk.
2. Trustless Bridges
Trustless bridges use smart contracts and on-chain verification mechanisms to manage asset transfers. These include solutions like Wormhole (originally), Hop Protocol, and Connext. Trustless designs aim to minimize human intervention and rely on cryptographic proofs, such as light clients or zk-SNARKs, to verify transactions. Although more decentralized, they involve higher gas costs and are more complex to implement securely.
3. Hybrid Approaches
Some modern bridges adopt a hybrid model combining trusted relayers with on-chain validation. LayerZero, for instance, uses Ultra Light Nodes and relies on both an oracle and a relayer to confirm message delivery. This model attempts to balance scalability, cost-efficiency, and decentralization but introduces new attack vectors if either party is compromised.
Strengths and Weaknesses of Bridge Technologies
Each bridge architecture presents unique trade-offs:
1. Trusted Bridges
– *Pros*: High throughput, low latency, easy integration
– *Cons*: Centralized trust, vulnerable to validator compromise (e.g., Ronin Bridge hack, $625M lost)
2. Trustless Bridges
– *Pros*: Decentralized, censorship-resistant
– *Cons*: Expensive gas fees, complex implementation, slower finality
3. Hybrid Bridges
– *Pros*: Flexible design, balance of performance and security
– *Cons*: Complex trust assumptions, dual points of failure
Case Study: In February 2022, Wormhole lost over $320M in ETH due to an exploit in its Solana smart contract, where attackers bypassed signature verification. This highlighted the importance of rigorous smart contract audits and runtime validation.
Recommendations for Evaluating Bridge Security
Before interacting with or integrating a cross-chain bridge, consider the following criteria:
1. Audits and Open Source Code
– Ensure the bridge has undergone multiple independent security audits and maintains public code repositories for transparency.
2. Validator Set Transparency
– Evaluate who controls the bridge’s validator nodes or relayers. The more decentralized and transparent, the better.
3. Fallback Mechanisms and Upgradability
– Check if the bridge includes safety features such as circuit breakers, rate limits, or emergency pause functions.
4. Bug Bounty Programs
– Platforms offering substantial bounties for discovering vulnerabilities demonstrate proactive security culture.
5. Cross-Chain Message Authenticity
– Review how message proof validation is handled. Bridges using cryptographic proofs (Merkle trees, zk-proofs) are less prone to spoofing.
Trends in Cross-Chain Bridge Security in 2025


As of 2025, the cross-chain ecosystem is evolving rapidly with a focus on higher security and efficiency:
1. Adoption of zk-Bridges
– Zero-knowledge (ZK) bridges are gaining traction due to their ability to compress large amounts of data into succinct proofs, enabling secure and scalable cross-chain verification. Projects like zkBridge and zkSync’s L3 initiatives are pioneering this space.
2. Standardization Efforts
– Interoperability standards such as the Interchain Messaging Standard (IMS) and ERC-5164 are being developed to create uniform security protocols across bridges.
3. Modular Bridge Design
– Developers are moving towards modular bridge stacks, separating execution, consensus, and data availability layers to mitigate systemic risks.
4. On-Chain Monitoring and AI Threat Detection
– Real-time threat monitoring tools powered by AI are being integrated into bridge infrastructure to detect anomalies and halt malicious activity proactively.
5. Cross-Chain Insurance Solutions
– To mitigate user risk, decentralized insurance protocols now offer protection specifically for cross-chain bridge failures, increasing user confidence.
Conclusion

Cross-chain bridges are indispensable for the future of a multi-chain blockchain ecosystem, but they come with inherent security challenges. A thorough understanding of different architectural models, their associated risks, and current best practices is essential for safe interaction. As the industry matures, innovations like zk-proofs and standardization efforts are expected to enhance the reliability of cross-chain communication. However, vigilance, continuous auditing, and community oversight remain critical components in securing these crucial components of web3 infrastructure.