1. Define the Scope of Your Crypto Workflow
Before setting up a multi-device crypto workflow, it’s essential to clearly define what your workflow entails. Are you actively trading, managing long-term holdings, interacting with DeFi protocols, or developing blockchain applications? Each use case implies different security needs. For example, a developer signing smart contracts daily faces higher exposure than a long-term investor who rarely moves funds.
Real-world case: A 2022 breach involved a Web3 developer who used the same hot wallet across multiple devices, including a testnet environment. An infected browser extension on one device leaked private keys, resulting in a $90,000 loss. This highlights the importance of isolating environments based on use cases.
Tip for beginners: Start by mapping out which devices interact with your crypto assets and why. This clarity helps segment risks and apply appropriate protections per device.
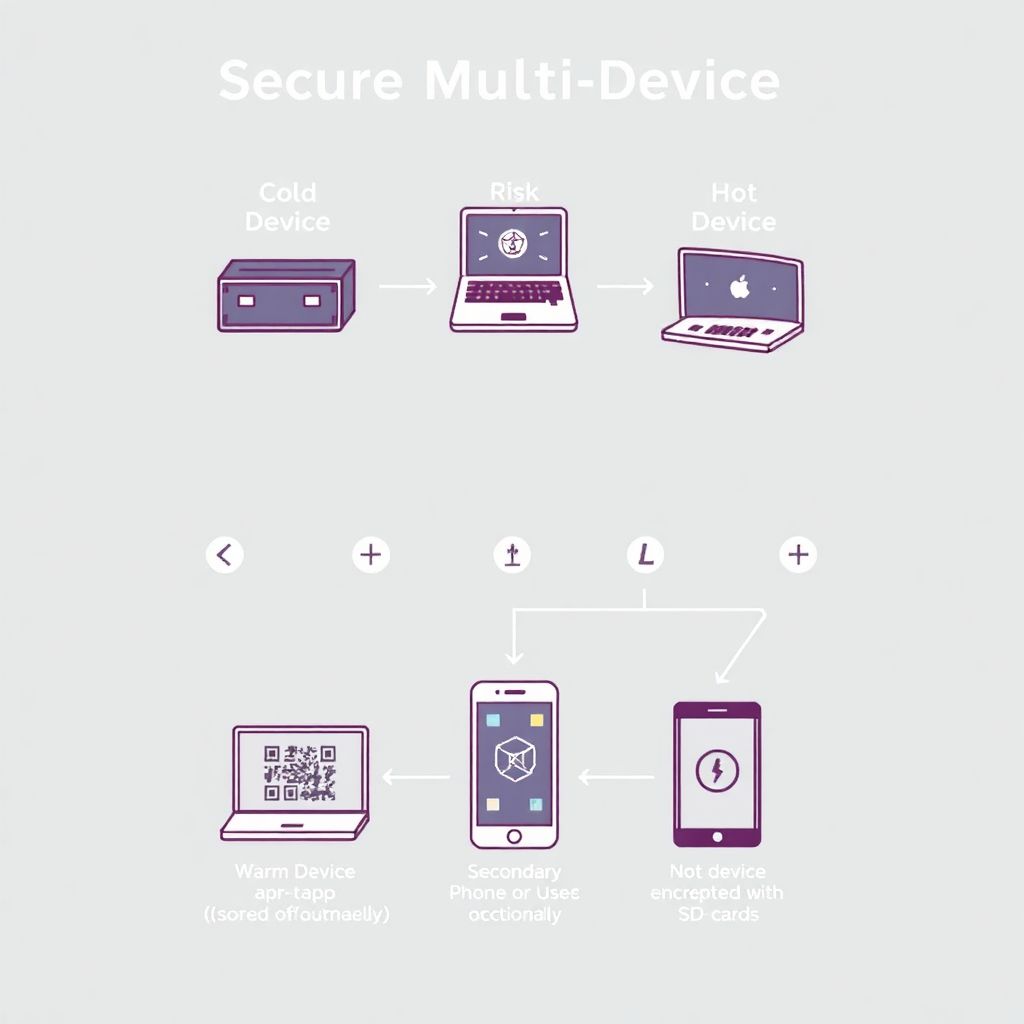
2. Segment Devices by Function and Risk
Not all devices should be treated equally. A major principle in cybersecurity is segmentation—separating functionally different environments to reduce attack vectors. For crypto, assign specific roles to each device:
1. Cold device: An air-gapped computer or hardware wallet for long-term storage.
2. Warm device: A secondary phone or PC used for occasional transactions with additional protections.
3. Hot device: A daily-use device (e.g., smartphone) for interacting with DeFi or NFT platforms, assumed to be less secure.
This layered approach ensures that a compromise on one device does not affect all funds or keys.
Warning: Avoid storing private keys or seed phrases in plaintext on any internet-connected device. Even cloud-synced note apps or screenshots have led to irreversible losses.
3. Use Dedicated Hardware Wallets
Hardware wallets like Ledger, Trezor, or Keystone act as physical devices that sign transactions without exposing private keys to the internet. They should be used exclusively with cold and warm devices. When used correctly, they reduce the risk of malware-based key theft.
Implementation steps:
1. Purchase directly from the manufacturer to avoid tampered devices.
2. Verify firmware integrity before first use.
3. Use a passphrase or hidden wallet feature for added protection.
Case study: In 2021, a crypto influencer lost $400,000 because their hardware wallet’s seed phrase was stored in a password manager that got compromised. This underscores the importance of keeping seed phrases offline and separated from digital systems.
4. Secure Communication Between Devices
Transferring data (e.g., signed transactions, addresses) between devices must be done securely. If you’re using a cold device that’s air-gapped, QR code transfers or SD cards should be vetted for integrity.
Best practices:
1. Use QR-based wallets like Keystone for air-gapped signing.
2. Avoid USB drives unless encrypted and virus-scanned.
3. Never rely on email or cloud services to transmit sensitive data.
Beginner insight: Don’t underestimate QR-based workflows; they’re not only secure but also user-friendly when configured correctly.
5. Regularly Update and Monitor Devices
Security is not static. Operating systems, wallets, and firmware require regular updates to patch vulnerabilities. However, updates should be approached cautiously.
1. Only download software from official sources.
2. Verify wallet signatures when possible.
3. Test updates on non-critical devices before deploying widely.
Real example: A 2023 exploit in a popular mobile wallet was patched within 48 hours. Users who delayed updates lost access to funds due to compatibility issues. Regular monitoring and proactive patching can prevent such scenarios.
6. Implement Multi-Factor Authentication and Account Segregation
For any account tied to your crypto activity—exchange accounts, developer platforms, or communication tools—enable multi-factor authentication (MFA) using hardware-based keys (e.g., YubiKey). Avoid SMS-based 2FA, as SIM swapping attacks remain prevalent.
Segment accounts across different emails and passwords. For instance:
1. Use a separate email for each exchange.
2. Employ password managers like Bitwarden or 1Password with strong master passwords.
3. Regularly audit access logs and revoke unused API keys or sessions.
Warning: Using the same password across multiple services exposes you to credential stuffing attacks, which are automated and increasingly common.
7. Establish a Recovery and Backup Plan
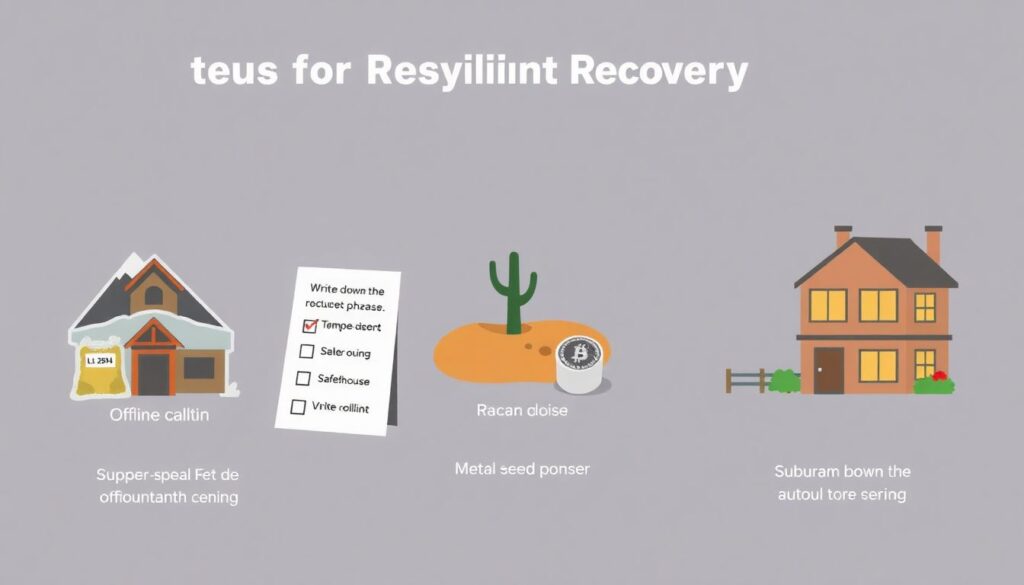
Even the most secure setup is incomplete without a clear recovery strategy. Store seed phrases and backup keys in multiple offline, geographically distinct locations. Use tamper-evident bags or metal seed storage solutions to prevent fire or water damage.
Steps for robust recovery:
1. Write down the seed phrase by hand.
2. Store one copy in a bank safety deposit box, and another with a trusted legal professional.
3. Periodically verify access but never expose the phrase to a digital device.
Case study: An early Bitcoiner lost access to $1.2 million worth of BTC when a single fire destroyed the only copy of their seed phrase. A distributed backup strategy could have prevented the loss.
8. Minimize Attack Surface by Limiting App Installations
Every additional browser extension, app, or plugin increases the potential for compromise. Only install vetted crypto-related tools. Avoid mixing personal and crypto activities on the same browser or device.
Advice: Use a hardened browser like Brave or Firefox with privacy extensions. Disable JavaScript on sensitive sites using add-ons like NoScript. For mobile, consider GrapheneOS or CalyxOS for enhanced control over permissions.
Warning for newcomers: The convenience of using a single device for everything is outweighed by the security risk. Separation is not overkill—it’s a necessity.
9. Educate Yourself Continuously

The crypto landscape evolves rapidly. New threats, phishing schemes, and malware emerge regularly. Participating in security forums, following white-hat researchers on Twitter, and reading official security advisories keeps your knowledge current.
Recommended practices:
1. Simulate phishing attempts using tools like Gophish to train your team.
2. Subscribe to newsletters like DeFiSafety or CertiK alerts.
3. Attend security-focused crypto webinars.
Final insight: Most crypto hacks are not due to sophisticated exploits but human error. Education remains your strongest defense.
Conclusion: Build Defensively, Think Proactively
A secure multi-device crypto workflow is not about owning the most expensive hardware or using the latest tools. It’s about thoughtful segmentation, consistent hygiene, and anticipating failure points. By treating each device as a potential vulnerability, applying strict operational discipline, and maintaining a recovery mindset, you substantially reduce your risk exposure. Crypto security is a mindset, not a one-time setup.