Historical Background
Wallet migrations have become increasingly common as users seek enhanced security, performance, and features with newer wallet solutions. Since 2022, the blockchain ecosystem has seen a surge in migrations due to software vulnerabilities, deprecation of older wallet versions, and the emergence of smart-contract wallets. According to Chainalysis, between 2022 and 2024, over $4.2 billion in crypto assets were moved during wallet migration events. However, more than $320 million was lost or stolen due to improper migration practices, phishing attacks, and mismanagement of private keys. This underscores the importance of a secure migration process.
Core Principles of Secure Wallet Migration
Protecting assets during wallet migration requires a strict adherence to foundational security principles. The most critical of these is maintaining absolute control over private keys or seed phrases. Users must never disclose their keys, even during migration, as this exposes assets to irrecoverable theft.
Key principles include:
– Cold storage usage: Transferring assets to a cold wallet before initiating migration can limit online exposure.
– Two-step verification: Enabling multi-factor authentication (MFA) on associated platforms reduces unauthorized access risks.
– Checksum validation: Verifying destination addresses using hash validation or QR code verification prevents misdirected transfers.
These practices, when systematically applied, mitigate the likelihood of compromise during the migration phase.
Practical Migration Workflows
Several secure workflows have emerged as industry standards. One widely adopted method is the staged migration process. It involves moving smaller test amounts before full transfers, allowing for detection of errors or compromised environments. For example, Ledger users migrating to a new hardware version often use Ledger Live to verify balances and ensure seamless restoration using BIP39 seed phrases.
Another method is the use of multisig wallets. In this scenario, assets are transferred to a 2-of-3 wallet, requiring multiple confirmations for fund movement. This creates an additional layer of assurance during migration. For institutional-grade users, platforms like Gnosis Safe or Fireblocks offer automated migration with audit trails and transaction pre-signing.
Best practice implementations include:
– Performing dry runs on testnets before transferring mainnet assets.
– Recording all steps via encrypted logs for traceability.
– Using reputable wallet software with open-source codebases to avoid backdoors.
Common Misconceptions
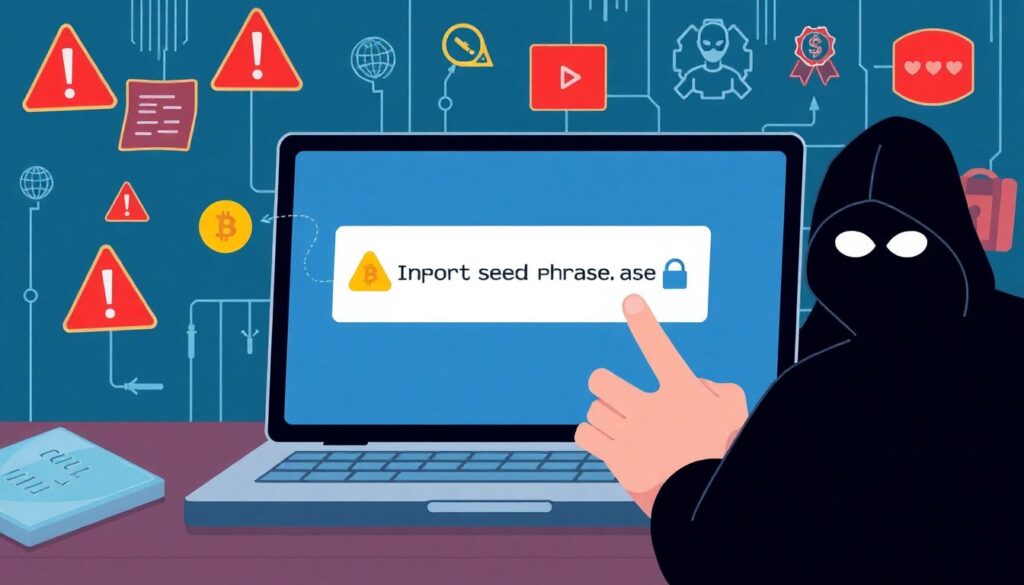
Despite the availability of migration tools, many users operate under flawed assumptions that jeopardize asset safety. A prevalent misconception is that importing a seed phrase into a new wallet is inherently safe. In reality, inputting a seed on an internet-connected device creates a vector for keylogging or clipboard exploits.
Additional false beliefs include:
– “Hardware wallets are unhackable”: While highly secure, they are vulnerable if the firmware is outdated or the supply chain is compromised.
– “Watching-only wallets are safe for migration”: These wallets can’t initiate transactions and are not suitable for full migrations without exposing private keys.
Users must also understand that not all wallets are compatible with every chain or token standard. For instance, attempting to import an Ethereum wallet into a Solana-native application can result in inaccessible funds without proper bridging or wrapping.
Conclusion

As the crypto landscape evolves, secure wallet migration is a critical practice for both new users and seasoned holders. With over $4 billion in assets moving across wallets in the last three years, the risks of improper migration are tangible and often irreparable. Adhering to core security principles, understanding protocol-specific limitations, and avoiding common misconceptions are essential steps toward a safe transition. Informed and methodical migrations not only protect digital wealth but also ensure long-term security and operability in decentralized ecosystems.